Friday, December 10. 2010
Notes from talk about GSM and free software
Yesterday I was at a talk at the FSFE Berlin about free software and GSM. It was an interesting talk and discussion.
Probably most of you know that GSM is the protocol that keeps the large majority of mobile phones running. In the past, only a handful of companies worked with the protocol and according to the talk, even most mobile phone companies don't know much of the internal details, as they usually buy ready-made chips.
Three free software projects work on GSM, OpenBTS and OpenBSC on the server side and OsmocomBB on the client side. What I didn't know yet and think is really remarkable: The Island State of Niue installed a GSM-network based on OpenBTS. The island found no commercial operator, so they installed a free software based and community supported GSM network.
Afterwards, we had a longer discussion about security and privacy implications of GSM. To sum it up, GSM is horribly broken on the security side. It offers no authentication between phones and cells. Also, it's encryption has been broken in the early 90s. There is not much progress in protocol improvements although this is known for a very long time. It's also well known that so-called IMSI-cachers are sold illegally for a few thousand dollars. The only reason GSM is still working at all is basically that those possibilities still cost a few thousands. But cheaper hardware and improvement in free GSM software makes it more likely that those possibilities will have a greater impact in the future (this is only a brief summary and I'm not really in that topic, see Wikipedia for some starting points for more info).
There was a bit of discussion about the question how realistic it is that some "normal user" is threatened by this due to the price of a few thousand dollars for the equipment. I didn't bring this up in the discussion any more, but I remember having seen a talk by a guy from Intel that the tendency is to design generic chips for various protocols that can be GSM, Bluetooth or WLAN purely by software control. Thinking about that, this raises the question of protocol security even more, as it might already be possible to use mainstream computer hardware to do mobile phone wiretapping by just replacing the firmware of a wireless lan card. It almost certainly will be possible within some years.
Another topic that was raised was frequency regulation. Even with free software you wouldn't be able to operate your own GSM network, because you couldn't afford buying a frequency (although it seems to be possible to get a testing license for a limited space, e. g. for technical workshops - the 27C3 will have a GSM test network). I mentioned that there's a chapter in the book "Code" from Lawrence Lessig (available in an updated version here, chapter is "The Regulators of Speech: Distribution" and starts on page 270 in the PDF). The thoughts from Lessing are that frequency regulation was neccessary in the beginning of radio technology, but today, it would be easily possible to design protocols that don't need regulation - they could be auto-regulating, e. g. with a prefix in front of every data package (the way wireless lan works). But the problem with that is that today, frequency usage generates large income for the state - that's completely against the original idea of it, as it's primarily purpose was to keep technology usable.
Probably most of you know that GSM is the protocol that keeps the large majority of mobile phones running. In the past, only a handful of companies worked with the protocol and according to the talk, even most mobile phone companies don't know much of the internal details, as they usually buy ready-made chips.
Three free software projects work on GSM, OpenBTS and OpenBSC on the server side and OsmocomBB on the client side. What I didn't know yet and think is really remarkable: The Island State of Niue installed a GSM-network based on OpenBTS. The island found no commercial operator, so they installed a free software based and community supported GSM network.
Afterwards, we had a longer discussion about security and privacy implications of GSM. To sum it up, GSM is horribly broken on the security side. It offers no authentication between phones and cells. Also, it's encryption has been broken in the early 90s. There is not much progress in protocol improvements although this is known for a very long time. It's also well known that so-called IMSI-cachers are sold illegally for a few thousand dollars. The only reason GSM is still working at all is basically that those possibilities still cost a few thousands. But cheaper hardware and improvement in free GSM software makes it more likely that those possibilities will have a greater impact in the future (this is only a brief summary and I'm not really in that topic, see Wikipedia for some starting points for more info).
There was a bit of discussion about the question how realistic it is that some "normal user" is threatened by this due to the price of a few thousand dollars for the equipment. I didn't bring this up in the discussion any more, but I remember having seen a talk by a guy from Intel that the tendency is to design generic chips for various protocols that can be GSM, Bluetooth or WLAN purely by software control. Thinking about that, this raises the question of protocol security even more, as it might already be possible to use mainstream computer hardware to do mobile phone wiretapping by just replacing the firmware of a wireless lan card. It almost certainly will be possible within some years.
Another topic that was raised was frequency regulation. Even with free software you wouldn't be able to operate your own GSM network, because you couldn't afford buying a frequency (although it seems to be possible to get a testing license for a limited space, e. g. for technical workshops - the 27C3 will have a GSM test network). I mentioned that there's a chapter in the book "Code" from Lawrence Lessig (available in an updated version here, chapter is "The Regulators of Speech: Distribution" and starts on page 270 in the PDF). The thoughts from Lessing are that frequency regulation was neccessary in the beginning of radio technology, but today, it would be easily possible to design protocols that don't need regulation - they could be auto-regulating, e. g. with a prefix in front of every data package (the way wireless lan works). But the problem with that is that today, frequency usage generates large income for the state - that's completely against the original idea of it, as it's primarily purpose was to keep technology usable.
Posted by Hanno Böck
in Computer culture, Cryptography, English, Linux, Security
at
22:35
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: 27c3, berlin, cellular, freesoftware, frequency, fsfe, gsm, lessig, mobilephones, openbsc, openbts, osmocombb, privacy, security, wiretapping
Thursday, December 2. 2010
Donkey Kong
 Recently, Nintendo released a new game called "Donkey Kong Country Returns" - I thought I'd take that as an opportunity to tell you a bit about it and it's main figure, Donkey Kong.
Recently, Nintendo released a new game called "Donkey Kong Country Returns" - I thought I'd take that as an opportunity to tell you a bit about it and it's main figure, Donkey Kong.What's interesting about this is that it's a revival of a revival - the original game is almost as old as I am (from 1981, so I can't tell you about the "good old times" here). It was released on an arcade machine and later ported to several consoles. You played Mario in the game (yes, this was also the very first time Mario appeared in a video game) and had to rescue the princess from a big evil Gorilla. Not very creative, but who cares about game stories anyway, right? You had to jump over barrels to get to the gorilla.
 I think the first time I saw the game was this one. It is from the Game and Watch series, mobile devices that had just one game built in. The Game and Watch games had no real display, they were only able to switch some elements on and of. For that limitation, the games had surprising complexity (another one I really liked is the Super Mario Bros. 3 wrist band game). Still, it is far away (or let's say rather different) from the original game.
I think the first time I saw the game was this one. It is from the Game and Watch series, mobile devices that had just one game built in. The Game and Watch games had no real display, they were only able to switch some elements on and of. For that limitation, the games had surprising complexity (another one I really liked is the Super Mario Bros. 3 wrist band game). Still, it is far away (or let's say rather different) from the original game.The second time I saw a Donkey Kong game was a (probably inofficial) remake in DOS. To be honest, it wasn't very good, but I had not many games at that time, so I played it a lot. You had to go up to the princess and after that, the gorilla threw something over the screen and you had to go down again, but now with fires and more holes. Sadly, I can't provide it to you as I didn't find it online (maybe I have it on an old CD, I'll have to look for that).
The very first time I played the "real" Donkey Kong was much later - 1992 Nintendo released the first two Donkey Kong games together as "Donkey Kong Classics" on the NES. There was also an advanced version for the Gameboy which featured the original Donkey Kong levels and about 100 more levels afterwards (I played through all of them).
1994 was the "first revival" - Nintendo released Donkey Kong Country on the Super Nintendo, a game which had impressive graphics and was a technical breakthrough at that time. It has not much in common with the original game beside the character and the fact that barrels still play an important role. A nice gimmick: It had a character called "Cranky Kong", who was said to be the "original Donkey Kong" from the old game. He was always grumbling that todays games are far to easy.
Now Nintendo is doing the second revival - interesting enough, it doesn't really use much of the possibilities the Wii offers. It is a classic jump and run game, very much like Donkey Kong Country (Nintendo just recently released "New Super Mario Bros", quite similar also a classic Mario jump and run). I like that. Though I played the game a bit and I must say I'm not highly impressed (at least yet). I'd rate it a nice game, but not a great game. But I also have to say that the old Donkey Kong Country is not on my all-time-favorite video games list. Maybe I'll tell you more when I played it longer.
What else? No blog about retro gaming without some links to really cool stuff:
A house with Donkey Kong design (does anyone know where this is?
Donkey Kong in Lego
(have more? post links in the comments)
Posted by Hanno Böck
in Computer culture, English, Retro Games
at
03:00
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: arcade, donkeykong, gameboy, games, mario, nes, nintendo, retrogames, retrogaming, videogames, wii
Friday, October 22. 2010
overheatd - is your CPU too hot?
Update: I got some nice hints in the comments. cpufreqd also includes this functionality and is probably the much more advanced solution. Also, I got a hint to linux-PHC, which allows undervolting a CPU and thus also saves energy.
I recently quite often had the problem that my system suddenly was shutting down. The reason was that when my processor got beyond 100 °C, my kernel decided that it's better to do so. I don't really know what caused this, but anyway, I needed a solution.
So i hacked together overheatd. A very effective way of cooling down a CPU is reducing its speed / frequency. Pretty much any modern CPU can do that and on Linux this can be controlled via the cpufreq interface. I wrote a little daemon that simply checks every 5 seconds (adjustable) if the temperature is over a certain treshold (90 °C default, also adjustable) and if yes, it sets cpufreq to the powersave governor (which means lowest speed possible). When the temperature is below or at 90 °C again, it's set back to the (default) ondemand governor. It also works for more than one CPU (I have a dual core), though it's very likely that it has bugs as soon as one goes beyond 10 CPUs - but I have no way to test this. Feel free to report bugs.
This could be made more sophisticated (not going to the lowest frequency but step by step to lower frequencies), but it does its job quite well for now. It might be a good idea to support something like this directly in the kernel (I wonder why that isn't the case already - it's pretty obvious), but that would probably involve a skilled kernel-hacker.
I recently quite often had the problem that my system suddenly was shutting down. The reason was that when my processor got beyond 100 °C, my kernel decided that it's better to do so. I don't really know what caused this, but anyway, I needed a solution.
So i hacked together overheatd. A very effective way of cooling down a CPU is reducing its speed / frequency. Pretty much any modern CPU can do that and on Linux this can be controlled via the cpufreq interface. I wrote a little daemon that simply checks every 5 seconds (adjustable) if the temperature is over a certain treshold (90 °C default, also adjustable) and if yes, it sets cpufreq to the powersave governor (which means lowest speed possible). When the temperature is below or at 90 °C again, it's set back to the (default) ondemand governor. It also works for more than one CPU (I have a dual core), though it's very likely that it has bugs as soon as one goes beyond 10 CPUs - but I have no way to test this. Feel free to report bugs.
This could be made more sophisticated (not going to the lowest frequency but step by step to lower frequencies), but it does its job quite well for now. It might be a good idea to support something like this directly in the kernel (I wonder why that isn't the case already - it's pretty obvious), but that would probably involve a skilled kernel-hacker.
Friday, October 1. 2010
Police violence for Stuttgart 21
Picture by Chris Grodotzki/Robin Wood
The project in question, Stuttgart 21, is the plan to bring Stuttgart's main train station underground. The current railhead station is planned to be replaced by a through station. The majority of the local population is opposed to that project for various reasons. The new station has only eight tracks while the current one has 16. Before the project has even started, the costs have more than doubled, currently five billion Euros are expected – but even the governor of Baden-Württemberg, Stefan Mappus, admitted that it probably will be more than seven billion. Critics expect it to be much more.
For that, local public transport services have been cut down in the area. Various other savings in social services were done in order to finance the megaproject, for example the subsidies for pupils' bus tickets have been cut. Stuttgart 21 is not a public transport project, it's a public transport cut down. It is mainly an urban construction project, because it will free a large area of rail tracks. The city's mayor Wolfgang Schuster promised a referendum after his last election if the costs of the project raise – he lied, the referendum never took place. Two years ago, environmentalists tried to enforce a referendum by collecting signatures. But it was not approved due to legal reasons – the laws for direct democracy in Baden-Württemberg are upon the worst in whole Germany.
In the park beside the station 300 trees need to be cut for the project. For that reason, activists from the envrionmental organization Robin Wood and others have built tree platforms in some of them in the past weeks. Many average people had declared in advance that they will take part on acts of civil dissobedience to protect the park and called themselves „Parkschützer“ (park protectors).
The violent operation took place on the 30th september. Thousands of policemen evicted the park with water cannons, pepper spray and police batons. In the night, about 20 trees got cut. Afterwards, the local Interior Minister Heribert Rech defended the police act by saying that the protestors had thrown stones. Some hours later he had to admit that this was a false information. Still, and despite of hundrets who got injured, he and the local governor Stefan Mappus from the CDU (conservative party) claimed the police act was completely legitimate.
For (german) information see:
http://www.kopfbahnhof-21.de/
http://www.parkschuetzer.de/
http://www.bei-abriss-aufstand.de/
Please feel free to copy this article or parts of it. I want this information to spread.
Posted by Hanno Böck
in Ecology, English, Politics
at
17:27
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: environment, mappus, police, policeviolence, protest, publictransport, rech, s21, schuster, stuttgart, stuttgart21, traffic
Thursday, September 9. 2010
Test your browser for Clickjacking protection
In 2008, a rather interesting new kind of security problem within web applications was found called Clickjacking. The idea is rather simple but genious: A webpage from the attacked web application is loaded into an iframe (a way to display a webpage within another webpage), but so small that the user cannot see it. Via javascript, this iframe is always placed below the mouse cursor and a button is focused in the iframe. When the user clicks anywhere on an attackers page, it clicks the button in his webapp causing some action the user didn't want to do.
What makes this vulnerability especially interesting is that it is a vulnerability within protocols and that it was pretty that there would be no easy fix without any changes to existing technology. A possible attempt to circumvent this would be a javascript frame killer code within every web application, but that's far away from being a nice solution (as it makes it neccessary to have javascript code around even if your webapp does not use any javascript at all).
Now, Microsoft suggested a new http header X-FRAME-OPTIONS that can be set to DENY or SAMEORIGIN. DENY means that the webpage sending that header may not be displayed in a frame or iframe at all. SAMEORIGIN means that it may only be referenced from webpages on the same domain name (sidenote: I tend to not like Microsoft and their behaviour on standards and security very much, but in this case there's no reason for that. Although it's not a standard – yet? - this proposal is completely sane and makes sense).
Just recently, Firefox added support, all major other browser already did that before (Opera, Chrome), so we finally have a solution to protect against clickjacking (konqueror does not support it yet and I found no plans for it, which may be a sign for the sad state of konqueror development regarding security features - they're also the only browser not supporting SNI). It's now up to web application developers to use that header. For most of them – if they're not using frames at all - it's probably quite easy, as they can just set the header to DENY all the time. If an app uses frames, it requires a bit more thoughts where to set DENY and where to use SAMEORIGIN.
It would also be nice to have some "official" IETF or W3C standard for it, but as all major browsers agree on that, it's okay to start using it now.
But the main reason I wrote this long introduction: I've set up a little test page where you can check if your browser supports the new header. If it doesn't, you should look for an update.
What makes this vulnerability especially interesting is that it is a vulnerability within protocols and that it was pretty that there would be no easy fix without any changes to existing technology. A possible attempt to circumvent this would be a javascript frame killer code within every web application, but that's far away from being a nice solution (as it makes it neccessary to have javascript code around even if your webapp does not use any javascript at all).
Now, Microsoft suggested a new http header X-FRAME-OPTIONS that can be set to DENY or SAMEORIGIN. DENY means that the webpage sending that header may not be displayed in a frame or iframe at all. SAMEORIGIN means that it may only be referenced from webpages on the same domain name (sidenote: I tend to not like Microsoft and their behaviour on standards and security very much, but in this case there's no reason for that. Although it's not a standard – yet? - this proposal is completely sane and makes sense).
Just recently, Firefox added support, all major other browser already did that before (Opera, Chrome), so we finally have a solution to protect against clickjacking (konqueror does not support it yet and I found no plans for it, which may be a sign for the sad state of konqueror development regarding security features - they're also the only browser not supporting SNI). It's now up to web application developers to use that header. For most of them – if they're not using frames at all - it's probably quite easy, as they can just set the header to DENY all the time. If an app uses frames, it requires a bit more thoughts where to set DENY and where to use SAMEORIGIN.
It would also be nice to have some "official" IETF or W3C standard for it, but as all major browsers agree on that, it's okay to start using it now.
But the main reason I wrote this long introduction: I've set up a little test page where you can check if your browser supports the new header. If it doesn't, you should look for an update.
Posted by Hanno Böck
in Code, English, Security
at
00:22
| Comment (1)
| Trackbacks (0)
Defined tags for this entry: browser, clickjacking, firefox, javascript, microsoft, security, vulnerability, websecurity
Tuesday, September 7. 2010
Trying to buy an ebook
For a while, I wanted to read the book "The Spirit Level" by Richard Wilkinson and Kate Pickett. But this blog entry is not about this book (I haven't read it yet). Since a while, I have such a nice ebook-reader (well, it's not that nice, read my older blogpost about it, but that's not my point here). I really hate it to carry around kilos of books and I also hate it to decide which books to take with me, so for the first time I tried to actually buy an ebook.
I found that penguin has this book. The price is 9,99 £ - interesting enough, the price for the paper variant is 7,99 £. Bits must be really expensive these days. Anyway, I thought 9,99 £ is still a price I was willing to pay, so I clicked on buying, created an account and so on. I was a bit confused when they asked me for the delivery adress, but hey, I don't mind. At the end, they told me that this book is not available for customers outside the UK.
I mean... it's hard for me to comment on that. How stupid is that? I really don't want to know the strange reason that might have be (I'm pretty sure it has something to do with international copyright law and collecting societies that are unable to arrive in the time of the internet, but I FUCKING DON'T CARE, I JUST WANT TO BUY A BOOK).
So I tried it further. Amazon has the book, but only for it's own ebook reader, the Kindle. All german bookstores I found only have the book on paper.
So - I still don't have the book. I could buy it on paper - but seriously, I don't want that. I bought an ebook-reader recently because I thought this gives me the freedom to read alternately in several books without carrying them around. I thought the time has come for that.
Maybe it's just that simple: The book publishing industry will have to die - just like the music industry, which sadly still refuses to do that finally.
(sidenote: I found that someone experienced nearly the same story - with the same book - and I even know that person. That happened purely by chance.)
I found that penguin has this book. The price is 9,99 £ - interesting enough, the price for the paper variant is 7,99 £. Bits must be really expensive these days. Anyway, I thought 9,99 £ is still a price I was willing to pay, so I clicked on buying, created an account and so on. I was a bit confused when they asked me for the delivery adress, but hey, I don't mind. At the end, they told me that this book is not available for customers outside the UK.
I mean... it's hard for me to comment on that. How stupid is that? I really don't want to know the strange reason that might have be (I'm pretty sure it has something to do with international copyright law and collecting societies that are unable to arrive in the time of the internet, but I FUCKING DON'T CARE, I JUST WANT TO BUY A BOOK).
So I tried it further. Amazon has the book, but only for it's own ebook reader, the Kindle. All german bookstores I found only have the book on paper.
So - I still don't have the book. I could buy it on paper - but seriously, I don't want that. I bought an ebook-reader recently because I thought this gives me the freedom to read alternately in several books without carrying them around. I thought the time has come for that.
Maybe it's just that simple: The book publishing industry will have to die - just like the music industry, which sadly still refuses to do that finally.
(sidenote: I found that someone experienced nearly the same story - with the same book - and I even know that person. That happened purely by chance.)
Posted by Hanno Böck
in Books, Computer culture, Copyright, English
at
22:12
| Comments (3)
| Trackbacks (0)
Tuesday, August 10. 2010
P != NP and what this may mean to cryptography
Yesterday I read via twitter that the HP researcher Vinay Deolalikar claimed to have proofen P!=NP. If you never heared about it, the question whether P=PN or not is probably the biggest unsolved problem in computer science and one of the biggest ones in mathematics. It's one of the seven millenium problems that the Clay Mathematics Institute announced in 2000. Only one of them has been solved yet (Poincaré conjecture) and everyone who solves one gets one million dollar for it.
The P/NP-problem is one of the candidates where many have thought that it may never be solved at all and if this result is true, it's a serious sensation. Obviously, that someone claimed to have solved it does not mean that it is solved. Dozends of pages with complex math need to be peer reviewed by other researchers. Even if it's correct, it will take some time until it'll be widely accepted. I'm far away from understanding the math used there, so I cannot comment on it, but it seems Vinay Deolalikar is a serious researcher and has published in the area before, so it's at least promising. As I'm currently working on "provable" cryptography and this has quite some relation to it, I'll try to explain it a bit in simple words and will give some outlook what this may mean for the security of your bank accounts and encrypted emails in the future.
P and NP are problem classes that say how hard it is to solve a problem. Generally speaking, P problems are ones that can be solved rather fast - more exactly, their running time can be expressed as a polynom. NP problems on the other hand are problems where a simple method exists to verify if they are correct but it's still hard to solve them. To give a real-world example: If you have a number of objects and want to put them into a box. Though you don't know if they fit into the box. There's a vast number of possibilitys how to order the objects so they fit into the box, so it may be really hard to find out if it's possible at all. But if you have a solution (all objects are in the box), you can close the lit and easily see that the solution works (I'm not entirely sure on that but I think this is a variant of KNAPSACK). There's another important class of problems and that are NP complete problems. Those are like the "kings" of NP problems, their meaning is that if you have an efficient algorithm for one NP complete problem, you would be able to use that to solve all other NP problems.
NP problems are the basis of cryptography. The most popular public key algorithm, RSA, is based on the factoring problem. Factoring means that you divide a non-prime into a number of primes, for example factoring 6 results in 2*3. It is hard to do factoring on a large number, but if you have two factors, it's easy to check that they are indeed factors of the large number by multiplying them. One big problem with RSA (and pretty much all other cryptographic methods) is that it's possible that a trick exists that nobody has found yet which makes it easy to factorize a large number. Such a trick would undermine the basis of most cryptography used in the internet today, for example https/ssl.
What one would want to see is cryptography that is provable secure. This would mean that one can proove that it's really hard (where "really hard" could be something like "this is not possible with normal computers using the amount of mass in the earth in the lifetime of a human") to break it. With todays math, such proofs are nearly impossible. In math terms, this would be a lower bound for the complexity of a problem.
And that's where the P!=NP proof get's interesting. If it's true that P!=NP then this would mean NP problems are definitely more complex than P problems. So this might be the first breakthrough in defining lower bounds of complexity. I said above that I'm currently working on "proovable" security (with the example of RSA-PSS), but provable in this context means that you have core algorithms that you believe are secure and design your provable cryptographic system around it. Knowing that P!=NP could be the first step in having really "provable secure" algorithms at the heart of cryptography.
I want to stress that it's only a "first step". Up until today, nobody was able to design a useful public key cryptography system around an NP hard problem. Factoring is NP, but (at least as far as we know) it's not NP hard. I haven't covered the whole topic of quantum computers at all, which opens up a whole lot of other questions (for the curious, it's unknown if NP hard problems can be solved with quantum computers).
As a final conclusion, if the upper result is true, this will lead to a whole new aera of cryptographic research - and some of it will very likely end up in your webbrowser within some years.
The P/NP-problem is one of the candidates where many have thought that it may never be solved at all and if this result is true, it's a serious sensation. Obviously, that someone claimed to have solved it does not mean that it is solved. Dozends of pages with complex math need to be peer reviewed by other researchers. Even if it's correct, it will take some time until it'll be widely accepted. I'm far away from understanding the math used there, so I cannot comment on it, but it seems Vinay Deolalikar is a serious researcher and has published in the area before, so it's at least promising. As I'm currently working on "provable" cryptography and this has quite some relation to it, I'll try to explain it a bit in simple words and will give some outlook what this may mean for the security of your bank accounts and encrypted emails in the future.
P and NP are problem classes that say how hard it is to solve a problem. Generally speaking, P problems are ones that can be solved rather fast - more exactly, their running time can be expressed as a polynom. NP problems on the other hand are problems where a simple method exists to verify if they are correct but it's still hard to solve them. To give a real-world example: If you have a number of objects and want to put them into a box. Though you don't know if they fit into the box. There's a vast number of possibilitys how to order the objects so they fit into the box, so it may be really hard to find out if it's possible at all. But if you have a solution (all objects are in the box), you can close the lit and easily see that the solution works (I'm not entirely sure on that but I think this is a variant of KNAPSACK). There's another important class of problems and that are NP complete problems. Those are like the "kings" of NP problems, their meaning is that if you have an efficient algorithm for one NP complete problem, you would be able to use that to solve all other NP problems.
NP problems are the basis of cryptography. The most popular public key algorithm, RSA, is based on the factoring problem. Factoring means that you divide a non-prime into a number of primes, for example factoring 6 results in 2*3. It is hard to do factoring on a large number, but if you have two factors, it's easy to check that they are indeed factors of the large number by multiplying them. One big problem with RSA (and pretty much all other cryptographic methods) is that it's possible that a trick exists that nobody has found yet which makes it easy to factorize a large number. Such a trick would undermine the basis of most cryptography used in the internet today, for example https/ssl.
What one would want to see is cryptography that is provable secure. This would mean that one can proove that it's really hard (where "really hard" could be something like "this is not possible with normal computers using the amount of mass in the earth in the lifetime of a human") to break it. With todays math, such proofs are nearly impossible. In math terms, this would be a lower bound for the complexity of a problem.
And that's where the P!=NP proof get's interesting. If it's true that P!=NP then this would mean NP problems are definitely more complex than P problems. So this might be the first breakthrough in defining lower bounds of complexity. I said above that I'm currently working on "proovable" security (with the example of RSA-PSS), but provable in this context means that you have core algorithms that you believe are secure and design your provable cryptographic system around it. Knowing that P!=NP could be the first step in having really "provable secure" algorithms at the heart of cryptography.
I want to stress that it's only a "first step". Up until today, nobody was able to design a useful public key cryptography system around an NP hard problem. Factoring is NP, but (at least as far as we know) it's not NP hard. I haven't covered the whole topic of quantum computers at all, which opens up a whole lot of other questions (for the curious, it's unknown if NP hard problems can be solved with quantum computers).
As a final conclusion, if the upper result is true, this will lead to a whole new aera of cryptographic research - and some of it will very likely end up in your webbrowser within some years.
Posted by Hanno Böck
in Computer culture, Cryptography, English, Science
at
12:42
| Comments (2)
| Trackbacks (0)
Defined tags for this entry: cmi, cryptography, deolalikar, math, milleniumproblems, pnp, provablesecurity, security
Friday, May 14. 2010
Secure RSA padding: RSA-PSS
I got selected for this years Google Summer of Code with a project for the implementation of RSA-PSS in the nss library. RSA-PSS will also be the topic of my diploma thesis, so I thought I'd write some lines about it.
RSA is, as you may probably know, the most widely used public key cryptography algorithm. It can be used for signing and encryption, RSA-PSS is about signing (something similar, RSA-OAEP, exists for encryption, but that's not my main topic).
The formula for the RSA-algorithm is S = M^k mod N (S is the signature, M the input, k the private key and N the product of two big prime numbers). One important thing is that M is not the Message itself, but some encoding of the message. A simple way of doing this encoding is using a hash-function, for example SHA256. This is basically how old standards (like PKCS #1 1.5) worked. While no attacks exist against this scheme, it's believed that this can be improved. One reason is that while the RSA-function accepts an input of size N (which is the same length as the keysize, for example 2048/4096 bit), hash-functions usually produce much smaller inputs (something like 160/256 bit).
An improved scheme for that is the Probabilistic Signature Scheme (PSS), (Bellare/Rogaway 1996/1998). PSS is "provable secure". It does not mean that the outcoming algorithm is "provable secure" (that's impossible with today's math), but that the outcome is as secure as the input algorithm RSA and the used hash function (so-called "random oracle model"). A standard for PSS-encryption is PKCS #1 2.1 (republished as RFC 3447) So PSS in general is a good idea as a security measure, but as there is no real pressure to implement it, it's still not used very much. Just an example, the new DNSSEC ressource records just published last year still use the old PKCS #1 1.5 standard.
For SSL/TLS, standards to use PSS exist (RFC 4055, RFC 5756), but implementation is widely lacking. Just recently, openssl got support for PSS verification. The only implementation of signature creation I'm aware of is the java-library bouncycastle (yes, this forced me to write some lines of java code).
The nss library is used by the Mozilla products (Firefox, Thunderbird), so an implementation there is crucial for a more widespread use of PSS.
RSA is, as you may probably know, the most widely used public key cryptography algorithm. It can be used for signing and encryption, RSA-PSS is about signing (something similar, RSA-OAEP, exists for encryption, but that's not my main topic).
The formula for the RSA-algorithm is S = M^k mod N (S is the signature, M the input, k the private key and N the product of two big prime numbers). One important thing is that M is not the Message itself, but some encoding of the message. A simple way of doing this encoding is using a hash-function, for example SHA256. This is basically how old standards (like PKCS #1 1.5) worked. While no attacks exist against this scheme, it's believed that this can be improved. One reason is that while the RSA-function accepts an input of size N (which is the same length as the keysize, for example 2048/4096 bit), hash-functions usually produce much smaller inputs (something like 160/256 bit).
An improved scheme for that is the Probabilistic Signature Scheme (PSS), (Bellare/Rogaway 1996/1998). PSS is "provable secure". It does not mean that the outcoming algorithm is "provable secure" (that's impossible with today's math), but that the outcome is as secure as the input algorithm RSA and the used hash function (so-called "random oracle model"). A standard for PSS-encryption is PKCS #1 2.1 (republished as RFC 3447) So PSS in general is a good idea as a security measure, but as there is no real pressure to implement it, it's still not used very much. Just an example, the new DNSSEC ressource records just published last year still use the old PKCS #1 1.5 standard.
For SSL/TLS, standards to use PSS exist (RFC 4055, RFC 5756), but implementation is widely lacking. Just recently, openssl got support for PSS verification. The only implementation of signature creation I'm aware of is the java-library bouncycastle (yes, this forced me to write some lines of java code).
The nss library is used by the Mozilla products (Firefox, Thunderbird), so an implementation there is crucial for a more widespread use of PSS.
Posted by Hanno Böck
in Code, Cryptography, English, Linux, Security
at
23:22
| Comments (0)
| Trackbacks (0)
Monday, April 5. 2010
Easterhegg in Munich
 I visited this year's easterhegg in Munich. The easterhegg is an event by the chaos computer club.
I visited this year's easterhegg in Munich. The easterhegg is an event by the chaos computer club.I held a talk expressing some thoughts I had in mind for quite a long time about free licenses. The conclusion is mainly that I think it very often may make more sense to use public domain "licensing" instead of free licenses with restrictions. The slides can be downloaded here (video recording here in high quality / 1024x576 and here in lower quality / 640x360). Talk was in german, but the slides are english. I plan to write down a longer text about the subject, but I don't know when I'll find time for that.
I also had a 5 minute lightning-talk about RSA-PSS and RSA-OAEP, slides are here (german). I will probably write my diploma thesis about PSS, so you may read more about that here in the future.
From the other talks, I want to mention one because I think it's a very interesting project about an important topic: The mySmartGrid project is working on an opensource based solution for local smart grids. It's a research project by Fraunhofer ITWM Kaiserslautern and it sounds very promising. Smart grids will almost definitely come within the next years and if people stick to the solutions provided by big energy companies, this will most likely be a big thread to privacy and will most probably prefer old centralized electricity generation.
Posted by Hanno Böck
in Code, Computer culture, Copyright, Ecology, English, Politics, Security
at
20:58
| Comments (4)
| Trackbacks (0)
Defined tags for this entry: ccc, copyright, easterhegg, licenses, mysmartgrid, publicdomain, rsa, rsaoaep, rsapss
Sunday, February 7. 2010
Free and open source developers meeting (FOSDEM)
 After reading a lot about interesting stuff happening at this years FOSDEM, I decided very short term to go there. The FOSDEM in Brussels is probably one of the biggest (if not the biggest at all) meetings of free software developers. Unlike similar events (like several Linuxtag-events in Germany), it's focus is mainly on developers, so the talks are more high level.
After reading a lot about interesting stuff happening at this years FOSDEM, I decided very short term to go there. The FOSDEM in Brussels is probably one of the biggest (if not the biggest at all) meetings of free software developers. Unlike similar events (like several Linuxtag-events in Germany), it's focus is mainly on developers, so the talks are more high level.My impressions from FOSDEM so far: There are much more people compared when I was here a few years ago, so it seems the number of free software developers is inceasing (which is great). The interest focus seems to be to extend free software to other areas. Embedded devices, the BIOS, open hardware (lot's of interest in 3D-printers).
Yesterday morning, there was a quite interesting talk by Richard Clayton about Phishing, Scam etc. with lots of statistics and info about the supposed business models behind it. Afterwards I had a nice chat with some developers from OpenInkpot. There was a big interest in the Coreboot-talk, so I (and many others) just didn't get in because it was full.
Later Gentoo-developer Petteri Räty gave a talk about "How to be a good upstream" and I'd suggest every free software developer to have a look on that (I'll put the link here later).
I've just attended a rather interesting talk about 3D-printers like RepRap and MakerBot.
Posted by Hanno Böck
in Code, Computer culture, Copyright, English, Gentoo, Life, Linux
at
10:34
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: fosdem fosdem2010 freesoftware linux reprap makerb
Monday, February 1. 2010
SSL-Certificates with SHA256 signature
At least since 2005 it's well known that the cryptographic hash function SHA1 is seriously flawed and it's only a matter of time until it will be broken. However, it's still widely used and it can be expected that it'll be used long enough to allow real world attacks (as it happened with MD5 before). The NIST (the US National Institute of Standards and Technology) suggests not to use SHA1 after 2010, the german BSI (Bundesamt für Sicherheit in der Informationstechnik) says they should've been fadet out by the end of 2009.
The probably most widely used encryption protocol is SSL. It is a protocol that can operate on top of many other internet protocols and is for example widely used for banking accounts.
As SSL is a pretty complex protocol, it needs hash functions at various places, here I'm just looking at one of them. The signatures created by the certificate authorities. Every SSL certificate is signed by a CA, even if you generate SSL certificates yourself, they are self-signed, meaning that the certificate itself is it's own CA. From what I know, despite the suggestions mentioned above no big CA will give you certificates signed with anything better than SHA1. You can check this with:
openssl x509 -text -in [your ssl certificate]
Look for "Signature Algorithm". It'll most likely say sha1WithRSAEncryption. If your CA is good, it'll show sha256WithRSAEncryption. If your CA is really bad, it may show md5WithRSAEncryption.
When asking for SHA256 support, you often get the answer that the software still has problems, it's not ready yet. When asking for more information I never got answers. So I tried it myself. On an up-to-date apache webserver with mod_ssl, it was no problem to install a SHA256 signed certificate based on a SHA256 signed test CA. All browsers I've tried (Firefox 3.6, Konqueror 4.3.5, Opera 10.10, IE8 and even IE6) had no problem with it. You can check it out at [removed]. You will get a certificate warning (obviously, as it's signed by my own test CA), but you'll be able to view the page. If you want to test it without warnings, you can also import the CA certificate.
I'd be interested if this causes any problems (on server or on client side), so please leave a comment if you are aware of any incompatibilities.
Update: By request in the comments, I've also created a SHA512 testcase.
Update 2: StartSSL wrote me that they tried providing SHA256-certificates about a year ago and had too many problems - it wasn't very specific but they mentioned that earlier Windows XP and Windows 2003 Server versions may have problems.
The probably most widely used encryption protocol is SSL. It is a protocol that can operate on top of many other internet protocols and is for example widely used for banking accounts.
As SSL is a pretty complex protocol, it needs hash functions at various places, here I'm just looking at one of them. The signatures created by the certificate authorities. Every SSL certificate is signed by a CA, even if you generate SSL certificates yourself, they are self-signed, meaning that the certificate itself is it's own CA. From what I know, despite the suggestions mentioned above no big CA will give you certificates signed with anything better than SHA1. You can check this with:
openssl x509 -text -in [your ssl certificate]
Look for "Signature Algorithm". It'll most likely say sha1WithRSAEncryption. If your CA is good, it'll show sha256WithRSAEncryption. If your CA is really bad, it may show md5WithRSAEncryption.
When asking for SHA256 support, you often get the answer that the software still has problems, it's not ready yet. When asking for more information I never got answers. So I tried it myself. On an up-to-date apache webserver with mod_ssl, it was no problem to install a SHA256 signed certificate based on a SHA256 signed test CA. All browsers I've tried (Firefox 3.6, Konqueror 4.3.5, Opera 10.10, IE8 and even IE6) had no problem with it. You can check it out at [removed]. You will get a certificate warning (obviously, as it's signed by my own test CA), but you'll be able to view the page. If you want to test it without warnings, you can also import the CA certificate.
I'd be interested if this causes any problems (on server or on client side), so please leave a comment if you are aware of any incompatibilities.
Update: By request in the comments, I've also created a SHA512 testcase.
Update 2: StartSSL wrote me that they tried providing SHA256-certificates about a year ago and had too many problems - it wasn't very specific but they mentioned that earlier Windows XP and Windows 2003 Server versions may have problems.
Posted by Hanno Böck
in Cryptography, English, Gentoo, Linux, Security
at
23:23
| Comments (15)
| Trackback (1)
Tuesday, January 26. 2010
Hanvon WISEreader N526 - hardware fine, software a desaster
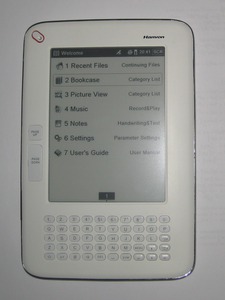 When asking me what I'd consider the most interesting technical developments in the near future, electronic books would be on the top of my list. So recently, I finally decided to buy one and ordered a Hanvon WISEreader N526. It has a pretty fair price, it seemed that free software support was likely to appear some time in the future (more on that later) and it has a touchscreen with pen, which was a feature I wanted to mark things in books.
When asking me what I'd consider the most interesting technical developments in the near future, electronic books would be on the top of my list. So recently, I finally decided to buy one and ordered a Hanvon WISEreader N526. It has a pretty fair price, it seemed that free software support was likely to appear some time in the future (more on that later) and it has a touchscreen with pen, which was a feature I wanted to mark things in books.From the hardware side, the device is pretty ok. Most ebook readers on the market share the same technologie for the display, it could have a bit more contrast, but else it's pretty okay. The device itself has a keyboard (which is querty, but not really ordered like a querty-keyboard), USB (not working as mass storage though), an audio output and a micro SD slot. Also, as said above, it has a touchscreen that can be used with a pen. So on the hardware side the device is quite fine.
What's not fine is the software running on it. It makes many features pretty much useless. Just to name a few flaws:
- Adding marks with the pen, one of the main features of the hardware, is pretty useless. It works neither on PDFs nor on epub files. It only works for TXT and HTML files, so it's not possible to do any marks on any layouted file format.
- HTML files are not supported. The vendor claims HTML support, but that's a plain lie. What it does is stripping out all HTML tags and showing the Text. If you know how HTML works, you can expect that this leads to pretty broken results and breaks all layout in HTML. Also, Hyperlinks don't work at all.
- The zooming capabilities are very limited. For text, you only have three zoom levels. All of them are far larger than normal text in a book. For PDF, it's possible to make it fit on height or width, but not anything in between.
- If you browse the files, there is no possibility to show the full filename, it only shows the beginning of the filename (about 20 characters). If you have files named “Author's name – Book title“ (which seems like a pretty common idea), you will only see some files with the author's name – not very useful.
- The device has a button for landscape view (turn the view 90°). But it doesn't work. Probably a bug.
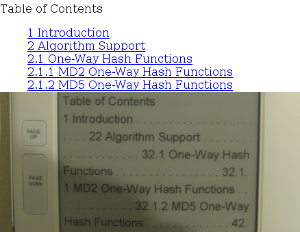
Example for HTML “support“ compared with original
Another thing I'm looking at is OpenInkpot. It's a free firmware for ebook devices and they are working on support for the N526. However, having talked to the developers it seems that support for the touchscreen/pen is pretty unsure, as the vendor refuses to provide any documentation for that. Also, as this is a volunteers project, it's not clear if and when proper support will be available.
Thursday, January 14. 2010
BIOS update by extracting HD image from ISO
Today I faced an interesting Linux problem that made me learn a couple of things I'd like to share. At first, we found an issue on a Thinkpad X301 notebook that was fixed in a newer BIOS version. So we wanted to do a BIOS update. Lenovo provides BIOS updates either for Windows or as bootable ISO CD-images. But the device had no CD-drive and only Linux installed. First we tried unetbootin, a tool to create bootable USB sticks out of ISO-Images. That didn't work.
So I had a deeper look at the ISO. What puzzled me was that when mounting it as a loopback device, there were no files on it. After some research I learned that there are different ways to create bootable CDs and one of them is the El Torito extension. It places an image of a harddisk on the CD, when booting, the image is loaded into memory and an OS can be executed (this probably only works for quite simple OSes like DOS, the Lenovo BIOS Upgrade disk is based on PC-DOS). There's a small PERL-script called geteltorito that is able to extract such images from ISO files.
It's possible to boot such harddisk images with grub and memdisk (part of syslinux). Install syslinux, place the file memdisk into /boot (found in /usr/lib/syslinux/ or /usr/share/syslinux/) and add something like this to your grub config:
Or for grub2:
Now you can select bios update in your boot menu and it should boot the BIOS upgrade utility.
(Note that this does not work for all Lenovo BIOS updates, only for those using an El Torito harddisk image - you can mount your iso with mount -o loop [path_to_iso] [mount_path] to check, if there are any files, this method is not for you)
So I had a deeper look at the ISO. What puzzled me was that when mounting it as a loopback device, there were no files on it. After some research I learned that there are different ways to create bootable CDs and one of them is the El Torito extension. It places an image of a harddisk on the CD, when booting, the image is loaded into memory and an OS can be executed (this probably only works for quite simple OSes like DOS, the Lenovo BIOS Upgrade disk is based on PC-DOS). There's a small PERL-script called geteltorito that is able to extract such images from ISO files.
It's possible to boot such harddisk images with grub and memdisk (part of syslinux). Install syslinux, place the file memdisk into /boot (found in /usr/lib/syslinux/ or /usr/share/syslinux/) and add something like this to your grub config:
title HD Image
root (hd0,0)
kernel /boot/memdisk
initrd /boot/image.img
root (hd0,0)
kernel /boot/memdisk
initrd /boot/image.img
Or for grub2:
menuentry "HD Image" {
set root=(hd0,2)
linux16 /boot/memdisk
initrd16 /boot/hdimage.img
}
set root=(hd0,2)
linux16 /boot/memdisk
initrd16 /boot/hdimage.img
}
Now you can select bios update in your boot menu and it should boot the BIOS upgrade utility.
(Note that this does not work for all Lenovo BIOS updates, only for those using an El Torito harddisk image - you can mount your iso with mount -o loop [path_to_iso] [mount_path] to check, if there are any files, this method is not for you)
Monday, August 24. 2009
Trip to the UK
I'm currently in Scottland on a trip through the UK. I'm trying to get some contacts to the much more active environmental movement here. For those who don't know, the UK has probably the most active climate movement in the world. I just came from a gathering in the Lake District and now I want to visit a protest site against open cast coal mining in Mainshill.
Afterwards I'll visit the Climate Camp.
It's quite interesting to see discussions here. The main topics at the moment are the third runway at the heathrow airport (see e. g. Plane Stupid) and the building of a new coal plant in Kingsnorth (done by the german company e-on). I heared quotes like »we shouldn't wait till they build the new plant, they're burning coal every day in the existing ones«, which is a large difference compared to the discussion in germany.
Afterwards I'll visit the Climate Camp.
It's quite interesting to see discussions here. The main topics at the moment are the third runway at the heathrow airport (see e. g. Plane Stupid) and the building of a new coal plant in Kingsnorth (done by the german company e-on). I heared quotes like »we shouldn't wait till they build the new plant, they're burning coal every day in the existing ones«, which is a large difference compared to the discussion in germany.
Posted by Hanno Böck
in Ecology, English, Life, Politics
at
15:45
| Comment (1)
| Trackbacks (0)
Defined tags for this entry: climate, climatecamp, co2, england, environment, klima, klimaschutz, klimawandel, kohle, kohlekraft, mainshill, scottland, uk, umwelt
Thursday, July 9. 2009
LPIC-1
 After passing the second exam at the Linuxtag, I'm now officially allowed to call myself LPIC-1.
After passing the second exam at the Linuxtag, I'm now officially allowed to call myself LPIC-1.
« previous page
(Page 9 of 23, totaling 335 entries)
» next page
