Saturday, July 21. 2012
And you thought 3D printers are useless
 Several years ago I bought a kind of very simple wardrobe from IKEA. It's called Bardu and is made out of steel rods and a plastic covering. It stands on wheels.
Several years ago I bought a kind of very simple wardrobe from IKEA. It's called Bardu and is made out of steel rods and a plastic covering. It stands on wheels.There are small plastic piece that connects the plastic rods with the wheels. And one of them broke a while back. I went to IKEA and asked for a replacement part. They told me that they don't ship parts for such old items - but they have an offering quite similar to the Bardu that I could buy. Sadly, the design has changed and the wheels are directly connected, so no compatible replacement part. The E-Mail service from IKEA told me the same: No replacement parts for old products.
At this point I could've complained about the fact that we live in a crazy world where someone suggests to you buying a new piece of furniture because a small plastic part of the old one is broken.
I posted a message in the RepRap-forum asking for help. If you don't know the RepRap: It's a 3D-printer, creating objects based on computer models out of simple plastic. The RepRap is an Open Source project built partly out of parts printed on other 3D printers. The idea is: Everyone can (with enough time and passion) built his own RepRap, all the documentation is available online.
I quickly got a response from someone from France who was willing to give it a try and re-create the needed plastic part on his 3D printer. Some message exchange later I sent him the broken and a non-broken part. Today, I got my RepRap-printed replacement part. It fits in perfectly. I'm seriously impressed.
Object on Thingiverse
Update (2012/12/11): I don't want to hide the fact that the whole issue turned out to be much trickier than thought. The original piece broke after a while. DeuxVis was so nice to experiment with likely more stable designs and sent me some more printed parts, but the first one already broke again. You can read the details in the RepRap-forum.
Posted by Hanno Böck
in Computer culture, Ecology, English, Life
at
21:50
| Comments (2)
| Trackbacks (0)
Friday, July 6. 2012
Leihen
 Ich spiele ja gelegentlich gerne ein gutes Videospiel. Und seit ungefähr 20 Jahren gerne jedes Spiel der Super Mario-Serie. Shigeru Miyamoto hat im vergangenen Jahr das neueste Werk fertiggestellt - Super Mario 3D Land. Die Videos, die ich gesehen hatte, sahen sehr vielversprechend aus.
Ich spiele ja gelegentlich gerne ein gutes Videospiel. Und seit ungefähr 20 Jahren gerne jedes Spiel der Super Mario-Serie. Shigeru Miyamoto hat im vergangenen Jahr das neueste Werk fertiggestellt - Super Mario 3D Land. Die Videos, die ich gesehen hatte, sahen sehr vielversprechend aus.Das Problem: Das Spiel ist für den Nintendo 3DS - und ich besitze keinen. Es ist nicht so, dass ich es mir nicht leisten könnte, mir so ein Gerät zu kaufen. Aber es erschien mir doch reichlich übertrieben - mit großer Warscheinlichkeit würde ich auf absehbare Zeit nur dieses eine Spiel spielen wollen. Wenn ich ein Spiel dann durchgespielt hab, ist mein Interesse, es nochmal zu spielen, in der Regel auch eher gering. Da der Nintendo 3DS noch relativ neu ist, ist auch ein gebrauchtes Gerät vergleichsweise teuer (etwas günstiger wird es auf ebay übrigens wenn man eins in Pink nimmt). Das hieße also eher abwarten, bis die Gebrauchtpreise in einigen Jahren günstig werden. Und überhaupt: Mein Interesse, die Menge an Zeug das in meiner Wohnung liegt und ich selten bis nie brauche, zu erhöhen, ist auch eher gering. Von jemand in meinem Bekanntenkreis, der einen 3DS hat, weiß ich gerade auch nicht.
Aber das große Internet ist so toll und hat eine Lösung für mich parat: Leihplattformen schießen gerade aus dem Boden - man nutzt Dinge gemeinsam und findet über das Internet Menschen, die gegen eine geringe Gebühr etwas ausleihen wollen. Bei leihdirwas.de habe ich mir - für einen sehr fairen Preis - einen 3DS mit Super Mario 3D Land geliehen. In meinem Fall quasi die perfekte Lösung.
Posted by Hanno Böck
in Computer culture, Life, Retro Games
at
00:33
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: 3ds, kokonsum, leihdirwas, leihen, nintendo, nintendo3ds, supermario, supermario3dland
Wednesday, March 28. 2012
Ancient streamed audio formats
I've promised that I'll dig into some old file formats and check how well they can be accessed on today's systems with free software.
Today, I'll start with audio formats. To begin, in general there are two kinds of audio formats. Streamed audio formats start with a more or less raw audio stream, apply some encoding and sometimes (lossless or lossy) compression. There are also tracker audio formats. They have internal information on tone pitches and instruments. Most really old computer audio files are tracker formats (like the popular C64 SID format). This blog post will be about streamed audio formats and I'll save the tracked ones for a later one.
The file formats I've chosen are more or less random, the main criteria being that I once stepped over them and still remember that. There's a hughe collection of all kinds of media file samples on the mplayer server.
The single most important project regarding exotic audio or video formats is ffmpeg, a library that does despite its name much more than decoding mpeg. All major free software media players use ffmpeg.
The file formats I've investigated:
Shorten playback has some problems, seeking often does not work, but this seems to be a limitation of the format itself. If I found feature requests for those formats, I've linked them, I also opened a bunch of them myself.
Conclusion: ffmpeg does a really fine job in playing all the obscure audio streaming formats. However, not every player that's based on ffmpeg plays every format ffmpeg can play. mplayer is the only player that succeeds with everything, probably because mplayer's devleopment is very tightly related to ffmpeg's development.
Update: I forgot to mention libav. It is a fork of ffmpeg. However, there's not that much to say, as ffmpeg and libav are still quite similar in their codec support. audacious does not support libav yet, all other apps just produce the same result.
Today, I'll start with audio formats. To begin, in general there are two kinds of audio formats. Streamed audio formats start with a more or less raw audio stream, apply some encoding and sometimes (lossless or lossy) compression. There are also tracker audio formats. They have internal information on tone pitches and instruments. Most really old computer audio files are tracker formats (like the popular C64 SID format). This blog post will be about streamed audio formats and I'll save the tracked ones for a later one.
The file formats I've chosen are more or less random, the main criteria being that I once stepped over them and still remember that. There's a hughe collection of all kinds of media file samples on the mplayer server.
The single most important project regarding exotic audio or video formats is ffmpeg, a library that does despite its name much more than decoding mpeg. All major free software media players use ffmpeg.
The file formats I've investigated:
- Some of the very first files distributing music through the Internet I remember were real audio files (extension .ra or .rm) from the german punk band WIZO. Real audio has a whole bunch of variants, scanning through some of my old backups, most of them used either AC-3 or Real Audio 2.0 as their codec. Thanks to Waybach Machine, you can still find the WIZO downloads (Raum der Zeit - Techno is AC-3, the others are RealAudio 2.0).
- vqf (or TwinVQ) was once announced having better quality than MP3 and was discussed as its successor. However, it seems it is almost completely distinct today, I didn't find anything at all (except in the above mentioned sample collection) in vqf format for download.
- Monkey's audio, extension .ape, is a lossless audio codec, which is itself licensed under some kind of noncommercial-use-only license that doesn't qualify as free software. It's not really old, as it's still being developed, but I added it as another example of an uncommon format.
- Shorten (extension shn) is an old lossless audio format, which was often used by the etree project that collects recordings of concerts. Today, it is mostly deprecated by flac, but the old recordings are still available.
- voc: The popular dos floppy copying program vgacopy had sound before I had a soundcard - it used the pc speaker to play .voc files it had shipped. It's a format used by some Creative software for their SoundBlaster. It's a more-or-less raw audio format like wav.
| mplayer | xine | vlc | audacious | totem/gstreamer | |
| ra AC3 | Yes | No Yes | Yes | Yes | No |
| ra 2.0 | Yes | No | No | Yes | No |
| vqf | Yes | No | Yes | Yes | No |
| ape | Yes | No | No | Yes | Yes |
| shn | Yes | Yes | No | Yes | Yes |
| voc | Yes | Scratchy | Scratchy | No | No |
Shorten playback has some problems, seeking often does not work, but this seems to be a limitation of the format itself. If I found feature requests for those formats, I've linked them, I also opened a bunch of them myself.
Conclusion: ffmpeg does a really fine job in playing all the obscure audio streaming formats. However, not every player that's based on ffmpeg plays every format ffmpeg can play. mplayer is the only player that succeeds with everything, probably because mplayer's devleopment is very tightly related to ffmpeg's development.
Update: I forgot to mention libav. It is a fork of ffmpeg. However, there's not that much to say, as ffmpeg and libav are still quite similar in their codec support. audacious does not support libav yet, all other apps just produce the same result.
Posted by Hanno Böck
in Computer culture, English, Gentoo, Linux, Music
at
01:17
| Comments (4)
| Trackbacks (0)
Tuesday, January 3. 2012
Old file formats
I recently had a discussion about the accessibility of today's computer content in the future. We started asking ourselves how well the support in current software is to read and use old legacy data formats - graphics, videos, text, layout documents, whatever may still be interesting today.
I remembered having such a discussion some years ago and back then, Works documents were mentioned by someone as a somewhat difficult format. Back then, libwps existed with some command line tools to convert to staroffice format (which could then be opened by openoffice) and experimental patches existed for openoffice itself. Seems at least here the situation has improved. The current version of libreoffice reads Works documents out of the box.
Free software projects play an important role in keeping old data accessible. Just to name two, ffmpeg does a great job in supporting a large number of old and exotic video formats. It's used by a bunch of popular video players like mplayer and vlc. For graphics files, there is imagemagick, which provides a conversion tool to up-to-date formats like PNG.
In some upcoming blog entries, I'll try to explore things, will look for old files and see if I am able to use them.
A call to my readers: Do you have any old stuff laying around that you'd find interesting to access today? Which file formats are difficult to access? Are you searching for tools to open / convert them? Do you have something old that might be worth publishing to others as well? Send me your stuff, I'm very interested.
I remembered having such a discussion some years ago and back then, Works documents were mentioned by someone as a somewhat difficult format. Back then, libwps existed with some command line tools to convert to staroffice format (which could then be opened by openoffice) and experimental patches existed for openoffice itself. Seems at least here the situation has improved. The current version of libreoffice reads Works documents out of the box.
Free software projects play an important role in keeping old data accessible. Just to name two, ffmpeg does a great job in supporting a large number of old and exotic video formats. It's used by a bunch of popular video players like mplayer and vlc. For graphics files, there is imagemagick, which provides a conversion tool to up-to-date formats like PNG.
In some upcoming blog entries, I'll try to explore things, will look for old files and see if I am able to use them.
A call to my readers: Do you have any old stuff laying around that you'd find interesting to access today? Which file formats are difficult to access? Are you searching for tools to open / convert them? Do you have something old that might be worth publishing to others as well? Send me your stuff, I'm very interested.
Wednesday, December 7. 2011
Keine Ahnung und das soll auch so bleiben

Versteht von solchen Dingen nichts: Gert Hoffmann (Quelle: Kontraesan / Wikipedia, Creative Commons by-sa by)
CDU-Oberbürgermeister und Ex-NPD-Mitglied Gert Hoffmann hat dazu folgendes mitzuteilen:
»Ich habe davon natürlich nichts gewusst, verstehe von solchen Dingen nichts und interessiere mich auch nicht dafür. Das wird auch so bleiben.«
Und nein, das ist keine Satire, sondern steht tatsächlich genau so in der Pressemitteilung der Stadt.
Posted by Hanno Böck
in Computer culture, Politics
at
19:31
| Comment (1)
| Trackbacks (0)
Defined tags for this entry: braunschweig, cdu, gerthoffmann, internetausdrucker, netzpolitik, piratenpartei, überwachung
Monday, October 10. 2011
Anti-virus applications and the Bundestrojaner
 Two days ago, the german Chaos Computer Club (CCC) published a sample that's supposedly a variant of a german state spy software (the so-called "Bundestrojaner").
Two days ago, the german Chaos Computer Club (CCC) published a sample that's supposedly a variant of a german state spy software (the so-called "Bundestrojaner").You might wonder if your anti virus software is protecting you. The webpage Virus Total lets you upload suspicious files, scans them with 43 different anti virus applications and presents you the result. Currently, 24 of 43 scanners detect the Bundestrojaner.
The CCC provides some further information where they state that the file they released is not the original one - they had several samples that differed and to avoid detection of the potential source, they changed the differing parts to something completely else. You might wonder if your anti virus app also detects the "original" Bundestrojaner and not just the modified file the CCC released.
We can easily check this if we change the modified pieces again to something else. A modified variant lowered the detection rate to 14 of 43 - amongst them the popular McAffee software. Now, it's pretty useless to only detect the exact published sample of a malware if we know that the original malware is different.
| Application | Version | Sig date | Modified sample | Original CCC sample |
|---|---|---|---|---|
| AhnLab-V3 | 2011.10.08.01 | 2011-Okt-09 | Trojan/Win32.R2d2 | Trojan/Win32.R2d2 |
| AntiVir | 7.11.15.175 | 2011-Okt-09 | TR/GruenFink.1 | TR/GruenFink.1 |
| Antiy-AVL | 2.0.3.7 | 2011-Okt-09 | - | - |
| Avast | 6.0.1289.0 | 2011-Okt-09 | Win32:Trojan-gen | Win32:Trojan-gen |
| AVG | 10.0.0.1190 | 2011-Okt-07 | - | - |
| BitDefender | 7.2 | 2011-Okt-10 | Backdoor.R2D2.A | Backdoor.R2D2.A |
| ByteHero | 1.0.0.1 | 2011-Sep-23 | - | - |
| CAT-QuickHeal | 11.00 | 2011-Okt-07 | - | - |
| ClamAV | 0.97.0.0 | 2011-Okt-10 | Trojan.BTroj-1 | Trojan.BTroj-1 |
| Commtouch | 5.3.2.6 | 2011-Okt-10 | - | W32/R2D2.A |
| Comodo | 10407 | 2011-Okt-10 | - | Backdoor.Win32.R2D2.A |
| DrWeb | 5.0.2.03300 | 2011-Okt-10 | - | - |
| Emsisoft | 5.1.0.11 | 2011-Okt-10 | Trojan.Win32.Bundestrojaner!A2 | Backdoor.Win32.R2D2!IK |
| eSafe | 7.0.17.0 | 2011-Okt-06 | - | - |
| eTrust-Vet | 36.1.8605 | 2011-Okt-07 | - | - |
| F-Prot | 4.6.2.117 | 2011-Okt-09 | - | W32/R2D2.A |
| F-Secure | 9.0.16440.0 | 2011-Okt-10 | Backdoor:W32/R2D2.A | Backdoor:W32/R2D2.A |
| Fortinet | 4.3.370.0 | 2011-Okt-10 | - | W32/R2D2.A!tr.bdr |
| GData | 22 | 2011-Okt-10 | Backdoor.R2D2.A | Backdoor.R2D2.A |
| Ikarus | T3.1.1.107.0 | 2011-Okt-10 | - | Backdoor.Win32.R2D2 |
| Jiangmin | 13.0.900 | 2011-Okt-09 | - | - |
| K7AntiVirus | 91155258 | 2011-Okt-08 | - | - |
| Kaspersky | 9.0.0.837 | 2011-Okt-09 | Backdoor.Win32.R2D2.a | Backdoor.Win32.R2D2.a |
| McAfee | 5.400.0.1158 | 2011-Okt-10 | - | Artemis!930712416770 |
| McAfee-GW-Edition | 2010.1D | 2011-Okt-09 | - | Artemis!930712416770 |
| Microsoft | 17702 | 2011-Okt-10 | Backdoor:Win32/R2d2.A | Backdoor:Win32/R2d2.A |
| NOD32 | 6529 | 2011-Okt-10 | Win32/R2D2.A | Win32/R2D2.A |
| Norman | 6.7.2011 | 2011-Okt-09 | - | - |
| nProtect | 2011-10-10.01 | 2011-Okt-10 | - | - |
| Panda | 10.0.3.5 | 2011-Okt-09 | - | Suspiciousfile |
| PCTools | 8.0.0.5 | 2011-Okt-10 | Backdoor.R2D2 | Backdoor.R2D2 |
| Prevx | 3.0 | 2011-Okt-10 | - | - |
| Rising | 23.78.06.02 | 2011-Okt-09 | - | - |
| Sophos | 4.70.0 | 2011-Okt-10 | Troj/BckR2D2-A | Troj/BckR2D2-A |
| SUPERAntiSpyware | 4.40.0.1006 | 2011-Okt-08 | - | - |
| Symantec | 20111.2.0.82 | 2011-Okt-10 | Backdoor.R2D2 | Backdoor.R2D2 |
| TheHacker | 6.7.0.1.318 | 2011-Okt-09 | - | - |
| TrendMicro | 9.500.0.1008 | 2011-Okt-09 | - | - |
| TrendMicro-HouseCall | 9.500.0.1008 | 2011-Okt-10 | - | BKDR_R2D2.A |
| VBA32 | 3.12.16.4 | 2011-Okt-07 | - | - |
| VIPRE | 10718 | 2011-Okt-10 | - | Trojan.Win32.Generic!BT |
| ViRobot | 2011.10.10.4710 | 2011-Okt-10 | - | - |
| VirusBuster | 14.1.3.0 | 2011-Okt-09 | - | - |
Scans done Monday morning around 8:00.
Posted by Hanno Böck
in Computer culture, English, Politics, Security
at
20:05
| Comments (0)
| Trackbacks (0)
Sunday, September 11. 2011
Michael S. Hart was a true visionary
 Michael S. Hart, the founder of Project Gutenberg, died some days ago.
Michael S. Hart, the founder of Project Gutenberg, died some days ago.Project Gutenberg, if you don't know, is a webpage collecting electronic books online. It was founded in 1971 (yes, long before the Internet as we know it today existed), when Hart typed the Declaration of Independency on a Xerox mainframe. Hart can be seen as the inventor of electronic books - 40 years ago.
We're still waiting for ebooks to get into mainstream. Currently, ebook reading devices are available, but their usage is not widespread yet. But I'm almost certain that ebooks will become very important within the next years. Hart had that opinion 40 years ago.
Today, Project Gutenberg has about 36.000 books. Most of them are public domain, because their copyright expired. There are other similar projects today: Wikisource is a sister project of Wikipedia and archive.org has a lot of scanned books, including most of the public domain books digitalized by Google.
Some mission statements for Project Gutenberg from Michael S. Hart (taken from Wikipedia) I find that sum up things very well:
"Encourage the Creation and Distribution of eBooks"
"Help Break Down the Bars of Ignorance and Illiteracy"
"Give As Many eBooks to As Many People As Possible"
Posted by Hanno Böck
in Books, Computer culture, Copyright, English
at
19:03
| Comment (1)
| Trackbacks (0)
Friday, September 9. 2011
Morgen Freiheit statt Angst: Auf die Straße!
Morgen findet die inzwischen schon traditionell zu nennende jährliche Demonstration „Freiheit statt Angst“ in Berlin statt. Seit 2007 gehen jährlich tausende Menschen unter diesem Motto für Datenschutz und digitale Bürgerrechte auf die Straße. Los geht es um 13:00 Uhr am Pariser Platz (Brandenburger Tor).

Angesichts der aktuellen Auseinandersetzungen – im Moment ist ja wieder die Vorratsdatenspeicherung ganz hoch im Kurs – möchte ich hier die Gelegenheit nutzen, zur Teilnahme aufzurufen.
Und für alle, denen Berlin zu weit ist, sei hier auch nochmals darauf verwiesen, dass zur Zeit eine Petition gegen die Wiedereinführung der Vorratsdatenspeicherung beim Bundestag läuft – die bislang leider mit etwa 20.000 Unterstützern noch nicht so gut läuft wie sie sollte. Aber es gibt auch gute Nachrichten: Einer Umfrage zu Folge spricht sich die Mehrheit der Bundesbürger gegen eine anlasslose Speicherung von Kommunikationsdaten aus.
 Einen Kritikpunkt möchte ich hier aber noch loswerden. Im vergangenen Jahr wurde die Demonstration von übermäßig vielen 9/11-Verschwörungstheoretikern heimgesucht – das ging so weit, dass ein englischsprachiger Artikel die Situation so darstellte, als sei es insgesamt eine Protestaktion von Verschwörungstheoretikern gewesen (was Unfug ist, es war eine Handvoll unter Tausenden). Einen ähnlich gelagerten Fall gab es bereits 2008 in Köln, als eine Datenschutzdemo von einer christlichen Sekte geradezu okkupiert wurde. Angesichts dieser Vorgeschichte finde ich es mehr als unglücklich, ausgerechnet Esoqueen Nina Hagen zur diesjährigen Demonstration einzuladen. Die hat nämlich zu HAARP und UFOs auch eher interessante Ansichten und ist mir bislang nicht durch intelligente politische Analysen aufgefallen.
Einen Kritikpunkt möchte ich hier aber noch loswerden. Im vergangenen Jahr wurde die Demonstration von übermäßig vielen 9/11-Verschwörungstheoretikern heimgesucht – das ging so weit, dass ein englischsprachiger Artikel die Situation so darstellte, als sei es insgesamt eine Protestaktion von Verschwörungstheoretikern gewesen (was Unfug ist, es war eine Handvoll unter Tausenden). Einen ähnlich gelagerten Fall gab es bereits 2008 in Köln, als eine Datenschutzdemo von einer christlichen Sekte geradezu okkupiert wurde. Angesichts dieser Vorgeschichte finde ich es mehr als unglücklich, ausgerechnet Esoqueen Nina Hagen zur diesjährigen Demonstration einzuladen. Die hat nämlich zu HAARP und UFOs auch eher interessante Ansichten und ist mir bislang nicht durch intelligente politische Analysen aufgefallen.
Aber nichtsdestotrotz: Die Themen sind verdammt wichtig, die Gegenseite schläft nicht. Also: Morgen auf die Straße!

Angesichts der aktuellen Auseinandersetzungen – im Moment ist ja wieder die Vorratsdatenspeicherung ganz hoch im Kurs – möchte ich hier die Gelegenheit nutzen, zur Teilnahme aufzurufen.
Und für alle, denen Berlin zu weit ist, sei hier auch nochmals darauf verwiesen, dass zur Zeit eine Petition gegen die Wiedereinführung der Vorratsdatenspeicherung beim Bundestag läuft – die bislang leider mit etwa 20.000 Unterstützern noch nicht so gut läuft wie sie sollte. Aber es gibt auch gute Nachrichten: Einer Umfrage zu Folge spricht sich die Mehrheit der Bundesbürger gegen eine anlasslose Speicherung von Kommunikationsdaten aus.
 Einen Kritikpunkt möchte ich hier aber noch loswerden. Im vergangenen Jahr wurde die Demonstration von übermäßig vielen 9/11-Verschwörungstheoretikern heimgesucht – das ging so weit, dass ein englischsprachiger Artikel die Situation so darstellte, als sei es insgesamt eine Protestaktion von Verschwörungstheoretikern gewesen (was Unfug ist, es war eine Handvoll unter Tausenden). Einen ähnlich gelagerten Fall gab es bereits 2008 in Köln, als eine Datenschutzdemo von einer christlichen Sekte geradezu okkupiert wurde. Angesichts dieser Vorgeschichte finde ich es mehr als unglücklich, ausgerechnet Esoqueen Nina Hagen zur diesjährigen Demonstration einzuladen. Die hat nämlich zu HAARP und UFOs auch eher interessante Ansichten und ist mir bislang nicht durch intelligente politische Analysen aufgefallen.
Einen Kritikpunkt möchte ich hier aber noch loswerden. Im vergangenen Jahr wurde die Demonstration von übermäßig vielen 9/11-Verschwörungstheoretikern heimgesucht – das ging so weit, dass ein englischsprachiger Artikel die Situation so darstellte, als sei es insgesamt eine Protestaktion von Verschwörungstheoretikern gewesen (was Unfug ist, es war eine Handvoll unter Tausenden). Einen ähnlich gelagerten Fall gab es bereits 2008 in Köln, als eine Datenschutzdemo von einer christlichen Sekte geradezu okkupiert wurde. Angesichts dieser Vorgeschichte finde ich es mehr als unglücklich, ausgerechnet Esoqueen Nina Hagen zur diesjährigen Demonstration einzuladen. Die hat nämlich zu HAARP und UFOs auch eher interessante Ansichten und ist mir bislang nicht durch intelligente politische Analysen aufgefallen.Aber nichtsdestotrotz: Die Themen sind verdammt wichtig, die Gegenseite schläft nicht. Also: Morgen auf die Straße!
Posted by Hanno Böck
in Computer culture, Politics
at
18:58
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: bürgerrechte, datenschutz, freiheitstattangst, ninahagen, verschwörungstheorien, vorratsdatenspeicherung
Friday, August 12. 2011
OpenLeaks doing strange things with SSL
 OpenLeaks is a planned platform like WikiLeaks, founded by ex-Wikileaks member Daniel Domscheit-Berg. It's been announced a while back and a beta is currently presented in cooperation with the newspaper taz during the Chaos Communication Camp (where I am right now).
OpenLeaks is a planned platform like WikiLeaks, founded by ex-Wikileaks member Daniel Domscheit-Berg. It's been announced a while back and a beta is currently presented in cooperation with the newspaper taz during the Chaos Communication Camp (where I am right now).I had a short look and found some things noteworthy:
The page is SSL-only, any connection attempt with http will be forwarded to https. When I opened the page in firefox, I got a message that the certificate is not valid. That's obviously bad, although most people probably won't see this message.
What is wrong here is that an intermediate certificate is missing - we have a so-called transvalid certificate (the term "transvalid" has been used for it by the EFF SSL Observatory project). Firefox includes the root certificate from Go Daddy, but the certificate is signed by another certificate which itself is signed by the root certificate. To make this work, one has to ship the so-called intermediate certificate when opening an SSL connection.
The reason why most people won't see this warning and why it probably went unnoticed is that browsers remember intermediate certificates. If someone ever was on a webpage which uses the Go Daddy intermediate certificate, he won't see this warning. I saw it because I usually don't use Firefox and it had a rather fresh configuration.
There was another thing that bothered me: On top of the page, there's a line "Before submitting anything verify that the fingerprints of the SSL certificate match!" followed by a SHA-1 certificate fingerprint. Beside the fact that it's english on a german page, this is a rather ridiculous suggestion. Checking a fingerprint of an SSL connection against one you got through exactly that SSL connection is bogus. Checking a certificate fingerprint doesn't make any sense if you got it through a connection that was secured with that certificate. If checking a fingerprint should make sense, it has to come through a different channel. Beside that, nowhere is explained how a user should do that and what a fingerprint is at all. I doubt that this is of any help for the targetted audience by a whistleblower platform - it will probably only confuse people.
Both issues give me the impression that the people who designed OpenLeaks don't really know how SSL works - and that's not a good sign.
Posted by Hanno Böck
in Computer culture, Cryptography, English, Security
at
17:26
| Comments (6)
| Trackbacks (2)
Monday, May 2. 2011
DIY recycling: High quality magnets from harddisks
 I have a magnet plate hanging over my desk. Usually, the normal magnets for that purpose you can buy in shops are of very low quality and not very strong and fail to hold more than a few pieces of paper.
I have a magnet plate hanging over my desk. Usually, the normal magnets for that purpose you can buy in shops are of very low quality and not very strong and fail to hold more than a few pieces of paper.I recently discovered a way to get much better magnets almost for free: From old harddisks. To open a harddisks, you will usually need some kind of Torx screwdriver. Inside, you will find one or two very strong neodym magnets, which were originally used to move the read head.
Posted by Hanno Böck
in Computer culture, Ecology, English, Life
at
17:24
| Comments (0)
| Trackbacks (0)
Wednesday, March 23. 2011
Review on Pioneer One
 Pioneer One is a science fiction series. What's special about it: It's completely supported by donations and it's distributed via BitTorrent. It comes under a Creative Commons Attribution-NonCommercial-ShareAlike license.
Pioneer One is a science fiction series. What's special about it: It's completely supported by donations and it's distributed via BitTorrent. It comes under a Creative Commons Attribution-NonCommercial-ShareAlike license.I read about the first episode a while back, but I forgot about it. Recently, I stumbled upon it again and took the opportunity to watch it. Up until now, just two episodes are completed, Episode three is announced for 28th of March and Episode four is in production. Further episodes will depend on the donations they get.
The rough story: A space ship is coming down over Montana and lands in Canadian territory. It spreads radiation, so the first suspicion is that it might be a terrorist attack. They find a probably russian human inside the ship, unconscious, with signets from the Sovjet Union. Their suspicion: The Sovjet Union has sent humans to settle on Mars and this one is a child coming back. The case is investigated by members of the US department of homeland security.
I found it pretty good. You can see overall that it's an independent production (for example the offices just don't look like offices from the US department of homeland security), but that makes no odds. The storyline is exciting, the actors do their job pretty well, the characters are interesting. My favorite character until now is Zachary Walzer, a scientist who's been endorsing Mars missions to the US authorities for a long time.
From the story concept, I'm not sure how this will make a very long series. At the moment it sounds like at some point they know what's going on and then it may not be interesting any more. Though there were some hints in which direction it might get to continue the story after that. I'm looking forward to see more.
If I raised your interest, go ahead and download Pioneer One.
Posted by Hanno Böck
in Computer culture, Copyright, English, Movies
at
20:37
| Comments (0)
| Trackbacks (0)
Saturday, February 26. 2011
Playing with the EFF SSL Observatory
The Electronic Frontier Foundation is running a fascinating project called the SSL Observatory. What they basically do is quite simple: They collected all SSL certificates they could get via https (by scanning all possible IPs), put them in a database and made statistics with them.
For an introduction, watch their talk at the 27C3 - it's worth it. For example, they found a couple of "Extended Validation"-Certificates that clearly violated the rules for extended validation, including one 512-bit EV-certificate.
The great thing is: They provide the full mysql database for download. I took the time to import the thing locally and am now able to run my own queries against it.
Let's show some examples: I'm interested in crypto algorithms used in the wild, so I wanted to know which are used in the wild at all. My query:
And the result:
This query was only for the valid certs, meaning they were signed by any browser-supported certificate authority. Now I run the same query on the all_certs table, which contains every cert, including expired, self-signed or otherwise invalid ones:
For an introduction, watch their talk at the 27C3 - it's worth it. For example, they found a couple of "Extended Validation"-Certificates that clearly violated the rules for extended validation, including one 512-bit EV-certificate.
The great thing is: They provide the full mysql database for download. I took the time to import the thing locally and am now able to run my own queries against it.
Let's show some examples: I'm interested in crypto algorithms used in the wild, so I wanted to know which are used in the wild at all. My query:
SELECT `Signature Algorithm`, count(*) FROM valid_certs GROUP BY `Signature Algorithm` ORDER BY count(*);shows all signature algorithms used on the certificates.
And the result:
+--------------------------+----------+Nothing very surprising here. Seems nobody is using anything else than RSA. The most popular hash algorithm is SHA-1, followed by MD5. The transition to SHA-256 seems to go very slowly (btw., the most common argument I heared when asking CAs for SHA-256 certificates was that Windows XP before service pack 3 doesn't support that). The four MD2-certificates seem interesting, though even that old, it's still more secure than MD5 and provides a similar security margin as SHA-1, though support for it has been removed from a couple of security libraries some time ago.
| Signature Algorithm | count(*) |
+--------------------------+----------+
| sha512WithRSAEncryption | 1 |
| sha1WithRSA | 1 |
| md2WithRSAEncryption | 4 |
| sha256WithRSAEncryption | 62 |
| md5WithRSAEncryption | 29958 |
| sha1WithRSAEncryption | 1503333 |
+--------------------------+----------+
This query was only for the valid certs, meaning they were signed by any browser-supported certificate authority. Now I run the same query on the all_certs table, which contains every cert, including expired, self-signed or otherwise invalid ones:
+-------------------------------------------------------+----------+It seems quite some people are experimenting with DSA signatures. Interesting are the number of GOST-certificates. GOST was a set of cryptography standards by the former soviet union. Seems the number of people trying to use elliptic curves is really low (compared to the popularity they have and that if anyone cares for SSL performance, they may be a good catch). For the algorithms only showing numbers, 1.2.840.113549.1.1.10 is RSASSA-PSS (not detected by current openssl release versions), 1.3.6.1.4.1.5849.1.3.2 is also a GOST-variant (GOST3411withECGOST3410) and 1.2.840.113549.27.1.5 is unknown to google, so it must be something very special.
| Signature Algorithm | count(*) |
+-------------------------------------------------------+----------+
| 1.2.840.113549.27.1.5 | 1 |
| sha1 | 1 |
| dsaEncryption | 1 |
| 1.3.6.1.4.1.5849.1.3.2 | 1 |
| md5WithRSAEncryption ANDALSO md5WithRSAEncryption | 1 |
| ecdsa-with-Specified | 1 |
| dsaWithSHA1-old | 2 |
| itu-t ANDALSO itu-t | 2 |
| dsaWithSHA | 3 |
| 1.2.840.113549.1.1.10 | 4 |
| ecdsa-with-SHA384 | 5 |
| ecdsa-with-SHA512 | 5 |
| ripemd160WithRSA | 9 |
| md4WithRSAEncryption | 15 |
| sha384WithRSAEncryption | 24 |
| GOST R 34.11-94 with GOST R 34.10-94 | 25 |
| shaWithRSAEncryption | 50 |
| sha1WithRSAEncryption ANDALSO sha1WithRSAEncryption | 72 |
| rsaEncryption | 86 |
| md2WithRSAEncryption | 120 |
| GOST R 34.11-94 with GOST R 34.10-2001 | 378 |
| sha512WithRSAEncryption | 513 |
| sha256WithRSAEncryption | 2542 |
| dsaWithSHA1 | 2703 |
| sha1WithRSA | 60969 |
| md5WithRSAEncryption | 1354658 |
| sha1WithRSAEncryption | 4196367 |
+-------------------------------------------------------+----------+
Posted by Hanno Böck
in Computer culture, Cryptography, English, Science, Security
at
22:40
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: algorithm, certificate, cryptography, eff, observatory, pss, rsa, security, ssl
Tuesday, December 14. 2010
How I revoked my old PGP key
Prologue of this story: A very long time ago (2004 to be exact), I decided to create a new PGP / GnuPG key with 4096 bits (due to this talk). However, shortly after that, I had a hardware failure of my hard disc. The home was a dm-crypt partition with xfs. I was able to restore most data, but it seemed the key was lost. I continued to use my old key I had in a backup and the 4096 key was bitrotting on keyservers. And that always annoyed me. In the meantime, I found all private keys of old DOS (2.6.3i) and Windows (5.0) PGP keys I had created in the past and revoked them, but this 4096 key was still there.
I still have the hard disc in question and a couple of dumps I created during the data rescue back then. Today, I decided that I'll have to try restoring that key again. My strategy was not trying to do anything on the filesystem, but only operate within the image. Very likely the data must be there somewhere.
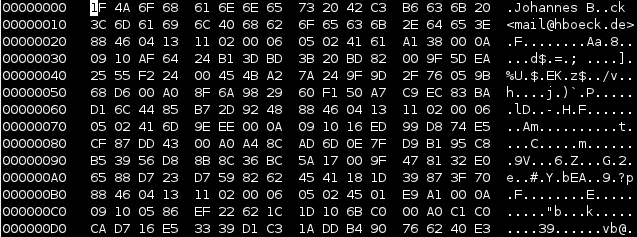
I found a place where I was rather sure that this must be the key. But exporting that piece with dd didn't succeed - looking a bit more at it, it seemed that the beginning was in shape, but at some place there were zeros. I don't know if this is due to the corruption or the fact that the filesystem didn't store the data sequentially at that place - but it didn't matter. I had a look at the file format of PGP keys in RFC 4880. Public keys and private keys are stored pretty similar. Only the beginning (the real "key") part differs, the userid / signatures / rest part is equal. So I was able to extract the private key block (starting with 0x95) with the rest (I just used the place where the first cleartext userid started with my name "Johannes"). What should I say? It worked like a charm. I was able to import my old private key and was able to revoke it. Key 147C5A9F is no longer valid. Great!
P. S.: Next step will be finally creating a new 4096 bit RSA key and abandoning my still-in-use 1024 bit DSA key for good.
I still have the hard disc in question and a couple of dumps I created during the data rescue back then. Today, I decided that I'll have to try restoring that key again. My strategy was not trying to do anything on the filesystem, but only operate within the image. Very likely the data must be there somewhere.

I found a place where I was rather sure that this must be the key. But exporting that piece with dd didn't succeed - looking a bit more at it, it seemed that the beginning was in shape, but at some place there were zeros. I don't know if this is due to the corruption or the fact that the filesystem didn't store the data sequentially at that place - but it didn't matter. I had a look at the file format of PGP keys in RFC 4880. Public keys and private keys are stored pretty similar. Only the beginning (the real "key") part differs, the userid / signatures / rest part is equal. So I was able to extract the private key block (starting with 0x95) with the rest (I just used the place where the first cleartext userid started with my name "Johannes"). What should I say? It worked like a charm. I was able to import my old private key and was able to revoke it. Key 147C5A9F is no longer valid. Great!
P. S.: Next step will be finally creating a new 4096 bit RSA key and abandoning my still-in-use 1024 bit DSA key for good.
Posted by Hanno Böck
in Code, Computer culture, Cryptography, English, Linux, Security
at
15:47
| Comment (1)
| Trackbacks (0)
Friday, December 10. 2010
Notes from talk about GSM and free software
Yesterday I was at a talk at the FSFE Berlin about free software and GSM. It was an interesting talk and discussion.
Probably most of you know that GSM is the protocol that keeps the large majority of mobile phones running. In the past, only a handful of companies worked with the protocol and according to the talk, even most mobile phone companies don't know much of the internal details, as they usually buy ready-made chips.
Three free software projects work on GSM, OpenBTS and OpenBSC on the server side and OsmocomBB on the client side. What I didn't know yet and think is really remarkable: The Island State of Niue installed a GSM-network based on OpenBTS. The island found no commercial operator, so they installed a free software based and community supported GSM network.
Afterwards, we had a longer discussion about security and privacy implications of GSM. To sum it up, GSM is horribly broken on the security side. It offers no authentication between phones and cells. Also, it's encryption has been broken in the early 90s. There is not much progress in protocol improvements although this is known for a very long time. It's also well known that so-called IMSI-cachers are sold illegally for a few thousand dollars. The only reason GSM is still working at all is basically that those possibilities still cost a few thousands. But cheaper hardware and improvement in free GSM software makes it more likely that those possibilities will have a greater impact in the future (this is only a brief summary and I'm not really in that topic, see Wikipedia for some starting points for more info).
There was a bit of discussion about the question how realistic it is that some "normal user" is threatened by this due to the price of a few thousand dollars for the equipment. I didn't bring this up in the discussion any more, but I remember having seen a talk by a guy from Intel that the tendency is to design generic chips for various protocols that can be GSM, Bluetooth or WLAN purely by software control. Thinking about that, this raises the question of protocol security even more, as it might already be possible to use mainstream computer hardware to do mobile phone wiretapping by just replacing the firmware of a wireless lan card. It almost certainly will be possible within some years.
Another topic that was raised was frequency regulation. Even with free software you wouldn't be able to operate your own GSM network, because you couldn't afford buying a frequency (although it seems to be possible to get a testing license for a limited space, e. g. for technical workshops - the 27C3 will have a GSM test network). I mentioned that there's a chapter in the book "Code" from Lawrence Lessig (available in an updated version here, chapter is "The Regulators of Speech: Distribution" and starts on page 270 in the PDF). The thoughts from Lessing are that frequency regulation was neccessary in the beginning of radio technology, but today, it would be easily possible to design protocols that don't need regulation - they could be auto-regulating, e. g. with a prefix in front of every data package (the way wireless lan works). But the problem with that is that today, frequency usage generates large income for the state - that's completely against the original idea of it, as it's primarily purpose was to keep technology usable.
Probably most of you know that GSM is the protocol that keeps the large majority of mobile phones running. In the past, only a handful of companies worked with the protocol and according to the talk, even most mobile phone companies don't know much of the internal details, as they usually buy ready-made chips.
Three free software projects work on GSM, OpenBTS and OpenBSC on the server side and OsmocomBB on the client side. What I didn't know yet and think is really remarkable: The Island State of Niue installed a GSM-network based on OpenBTS. The island found no commercial operator, so they installed a free software based and community supported GSM network.
Afterwards, we had a longer discussion about security and privacy implications of GSM. To sum it up, GSM is horribly broken on the security side. It offers no authentication between phones and cells. Also, it's encryption has been broken in the early 90s. There is not much progress in protocol improvements although this is known for a very long time. It's also well known that so-called IMSI-cachers are sold illegally for a few thousand dollars. The only reason GSM is still working at all is basically that those possibilities still cost a few thousands. But cheaper hardware and improvement in free GSM software makes it more likely that those possibilities will have a greater impact in the future (this is only a brief summary and I'm not really in that topic, see Wikipedia for some starting points for more info).
There was a bit of discussion about the question how realistic it is that some "normal user" is threatened by this due to the price of a few thousand dollars for the equipment. I didn't bring this up in the discussion any more, but I remember having seen a talk by a guy from Intel that the tendency is to design generic chips for various protocols that can be GSM, Bluetooth or WLAN purely by software control. Thinking about that, this raises the question of protocol security even more, as it might already be possible to use mainstream computer hardware to do mobile phone wiretapping by just replacing the firmware of a wireless lan card. It almost certainly will be possible within some years.
Another topic that was raised was frequency regulation. Even with free software you wouldn't be able to operate your own GSM network, because you couldn't afford buying a frequency (although it seems to be possible to get a testing license for a limited space, e. g. for technical workshops - the 27C3 will have a GSM test network). I mentioned that there's a chapter in the book "Code" from Lawrence Lessig (available in an updated version here, chapter is "The Regulators of Speech: Distribution" and starts on page 270 in the PDF). The thoughts from Lessing are that frequency regulation was neccessary in the beginning of radio technology, but today, it would be easily possible to design protocols that don't need regulation - they could be auto-regulating, e. g. with a prefix in front of every data package (the way wireless lan works). But the problem with that is that today, frequency usage generates large income for the state - that's completely against the original idea of it, as it's primarily purpose was to keep technology usable.
Posted by Hanno Böck
in Computer culture, Cryptography, English, Linux, Security
at
22:35
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: 27c3, berlin, cellular, freesoftware, frequency, fsfe, gsm, lessig, mobilephones, openbsc, openbts, osmocombb, privacy, security, wiretapping
Thursday, December 2. 2010
Donkey Kong
 Recently, Nintendo released a new game called "Donkey Kong Country Returns" - I thought I'd take that as an opportunity to tell you a bit about it and it's main figure, Donkey Kong.
Recently, Nintendo released a new game called "Donkey Kong Country Returns" - I thought I'd take that as an opportunity to tell you a bit about it and it's main figure, Donkey Kong.What's interesting about this is that it's a revival of a revival - the original game is almost as old as I am (from 1981, so I can't tell you about the "good old times" here). It was released on an arcade machine and later ported to several consoles. You played Mario in the game (yes, this was also the very first time Mario appeared in a video game) and had to rescue the princess from a big evil Gorilla. Not very creative, but who cares about game stories anyway, right? You had to jump over barrels to get to the gorilla.
 I think the first time I saw the game was this one. It is from the Game and Watch series, mobile devices that had just one game built in. The Game and Watch games had no real display, they were only able to switch some elements on and of. For that limitation, the games had surprising complexity (another one I really liked is the Super Mario Bros. 3 wrist band game). Still, it is far away (or let's say rather different) from the original game.
I think the first time I saw the game was this one. It is from the Game and Watch series, mobile devices that had just one game built in. The Game and Watch games had no real display, they were only able to switch some elements on and of. For that limitation, the games had surprising complexity (another one I really liked is the Super Mario Bros. 3 wrist band game). Still, it is far away (or let's say rather different) from the original game.The second time I saw a Donkey Kong game was a (probably inofficial) remake in DOS. To be honest, it wasn't very good, but I had not many games at that time, so I played it a lot. You had to go up to the princess and after that, the gorilla threw something over the screen and you had to go down again, but now with fires and more holes. Sadly, I can't provide it to you as I didn't find it online (maybe I have it on an old CD, I'll have to look for that).
The very first time I played the "real" Donkey Kong was much later - 1992 Nintendo released the first two Donkey Kong games together as "Donkey Kong Classics" on the NES. There was also an advanced version for the Gameboy which featured the original Donkey Kong levels and about 100 more levels afterwards (I played through all of them).
1994 was the "first revival" - Nintendo released Donkey Kong Country on the Super Nintendo, a game which had impressive graphics and was a technical breakthrough at that time. It has not much in common with the original game beside the character and the fact that barrels still play an important role. A nice gimmick: It had a character called "Cranky Kong", who was said to be the "original Donkey Kong" from the old game. He was always grumbling that todays games are far to easy.
Now Nintendo is doing the second revival - interesting enough, it doesn't really use much of the possibilities the Wii offers. It is a classic jump and run game, very much like Donkey Kong Country (Nintendo just recently released "New Super Mario Bros", quite similar also a classic Mario jump and run). I like that. Though I played the game a bit and I must say I'm not highly impressed (at least yet). I'd rate it a nice game, but not a great game. But I also have to say that the old Donkey Kong Country is not on my all-time-favorite video games list. Maybe I'll tell you more when I played it longer.
What else? No blog about retro gaming without some links to really cool stuff:
A house with Donkey Kong design (does anyone know where this is?
Donkey Kong in Lego
(have more? post links in the comments)
Posted by Hanno Böck
in Computer culture, English, Retro Games
at
03:00
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: arcade, donkeykong, gameboy, games, mario, nes, nintendo, retrogames, retrogaming, videogames, wii
« previous page
(Page 2 of 20, totaling 289 entries)
» next page