Sunday, June 15. 2014
Slides from cryptography workshop for web developers
I recently held a workshop about cryptography for web developers at the company Internations. I am publishing the slides here.
Part 1: Crypto and Web [PDF] [LaTeX], [Slideshare]
Part 2: How broken is TLS? [PDF] [LaTeX], [Slideshare]
Part 3: Don't do this yourself [PDF] [LaTeX], [Slideshare]
Part 4: Hashing, Tokens, Randomness [PDF] [LaTeX], [Slideshare]
Part 5: Don't believe the Crypto Hype [PDF] [LaTeX] [Slideshare]
Part 2 is the same talk I recently have at the Easterhegg conference about TLS.
Part 1: Crypto and Web [PDF] [LaTeX], [Slideshare]
Part 2: How broken is TLS? [PDF] [LaTeX], [Slideshare]
Part 3: Don't do this yourself [PDF] [LaTeX], [Slideshare]
Part 4: Hashing, Tokens, Randomness [PDF] [LaTeX], [Slideshare]
Part 5: Don't believe the Crypto Hype [PDF] [LaTeX] [Slideshare]
Part 2 is the same talk I recently have at the Easterhegg conference about TLS.
Posted by Hanno Böck
in Code, Cryptography, English, Security
at
13:49
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: crypto, cryptography, http, https, security, ssl, tls, web, websecurity
Wednesday, March 26. 2014
Extract base64-encoded images from CSS
I recently stepped upon a webpage where I wanted to extract an image. However, after saving the page with my browser I couldn't find any JPG or PNG file. After looking into this, I saw some CSS code that looked like this:
background-image:url("data:image/jpeg;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAgAQAAAABbAUdZAAAAE0lEQVR4AWNgYPj/n4oElU1jAADtvT/BfzVwSgAAAABJRU5ErkJggg==";
What this does is that it embeds a base64 encoded image file into the CSS layout. I found some tools to create such images, but I found none to extract them. It isn't very hard to extract such an image, I wrote a small bash script that will do and that I'd like to share:
Hope this helps others. If this script is copyrightable at all (which I doubt), I hereby release it (like the other content of my blog) as CC0 / Public Domain.
background-image:url("data:image/jpeg;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAgAQAAAABbAUdZAAAAE0lEQVR4AWNgYPj/n4oElU1jAADtvT/BfzVwSgAAAABJRU5ErkJggg==";
What this does is that it embeds a base64 encoded image file into the CSS layout. I found some tools to create such images, but I found none to extract them. It isn't very hard to extract such an image, I wrote a small bash script that will do and that I'd like to share:
#!/bin/shSave this as css2base64 and pass HTML or CSS files on the command line (e. g. css2base64 test.html test.css).
n=1
for i in `grep -ho "base64,[A-Za-z0-9+/=]*" $@|sed -e "s:base64,::g"`; do
echo $i | base64 -d > file_$n
n=`expr $n + 1`
done
Hope this helps others. If this script is copyrightable at all (which I doubt), I hereby release it (like the other content of my blog) as CC0 / Public Domain.
Wednesday, May 4. 2011
Diploma thesis on RSA-PSS finished
 Today I submitted my diploma thesis to my university.
Today I submitted my diploma thesis to my university.The thesis summarizes several months of investigation of the Probabilistic Signature Scheme (PSS). Traditionally, RSA signatures are done by hashing and then signing them. PSS is an improved, provable secure scheme to prepare a message before signing. The main focus was to investigate where PSS is implemented and used in real world cryptographic applications with a special focus on X.509.
During my work on that, I also implemented PSS signatures for the nss library in the Google Summer of Code 2010.
The thesis itself (including PDF and latex sources), patches for nss and everything else relevant can be found at
http://rsapss.hboeck.de.
Tuesday, December 14. 2010
How I revoked my old PGP key
Prologue of this story: A very long time ago (2004 to be exact), I decided to create a new PGP / GnuPG key with 4096 bits (due to this talk). However, shortly after that, I had a hardware failure of my hard disc. The home was a dm-crypt partition with xfs. I was able to restore most data, but it seemed the key was lost. I continued to use my old key I had in a backup and the 4096 key was bitrotting on keyservers. And that always annoyed me. In the meantime, I found all private keys of old DOS (2.6.3i) and Windows (5.0) PGP keys I had created in the past and revoked them, but this 4096 key was still there.
I still have the hard disc in question and a couple of dumps I created during the data rescue back then. Today, I decided that I'll have to try restoring that key again. My strategy was not trying to do anything on the filesystem, but only operate within the image. Very likely the data must be there somewhere.
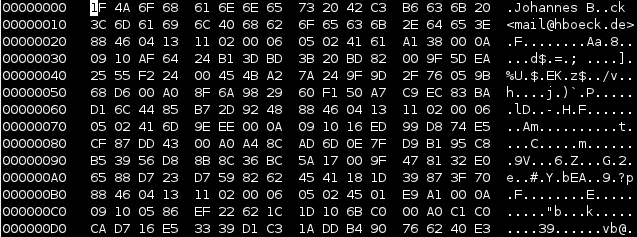
I found a place where I was rather sure that this must be the key. But exporting that piece with dd didn't succeed - looking a bit more at it, it seemed that the beginning was in shape, but at some place there were zeros. I don't know if this is due to the corruption or the fact that the filesystem didn't store the data sequentially at that place - but it didn't matter. I had a look at the file format of PGP keys in RFC 4880. Public keys and private keys are stored pretty similar. Only the beginning (the real "key") part differs, the userid / signatures / rest part is equal. So I was able to extract the private key block (starting with 0x95) with the rest (I just used the place where the first cleartext userid started with my name "Johannes"). What should I say? It worked like a charm. I was able to import my old private key and was able to revoke it. Key 147C5A9F is no longer valid. Great!
P. S.: Next step will be finally creating a new 4096 bit RSA key and abandoning my still-in-use 1024 bit DSA key for good.
I still have the hard disc in question and a couple of dumps I created during the data rescue back then. Today, I decided that I'll have to try restoring that key again. My strategy was not trying to do anything on the filesystem, but only operate within the image. Very likely the data must be there somewhere.

I found a place where I was rather sure that this must be the key. But exporting that piece with dd didn't succeed - looking a bit more at it, it seemed that the beginning was in shape, but at some place there were zeros. I don't know if this is due to the corruption or the fact that the filesystem didn't store the data sequentially at that place - but it didn't matter. I had a look at the file format of PGP keys in RFC 4880. Public keys and private keys are stored pretty similar. Only the beginning (the real "key") part differs, the userid / signatures / rest part is equal. So I was able to extract the private key block (starting with 0x95) with the rest (I just used the place where the first cleartext userid started with my name "Johannes"). What should I say? It worked like a charm. I was able to import my old private key and was able to revoke it. Key 147C5A9F is no longer valid. Great!
P. S.: Next step will be finally creating a new 4096 bit RSA key and abandoning my still-in-use 1024 bit DSA key for good.
Posted by Hanno Böck
in Code, Computer culture, Cryptography, English, Linux, Security
at
15:47
| Comment (1)
| Trackbacks (0)
Friday, October 22. 2010
overheatd - is your CPU too hot?
Update: I got some nice hints in the comments. cpufreqd also includes this functionality and is probably the much more advanced solution. Also, I got a hint to linux-PHC, which allows undervolting a CPU and thus also saves energy.
I recently quite often had the problem that my system suddenly was shutting down. The reason was that when my processor got beyond 100 °C, my kernel decided that it's better to do so. I don't really know what caused this, but anyway, I needed a solution.
So i hacked together overheatd. A very effective way of cooling down a CPU is reducing its speed / frequency. Pretty much any modern CPU can do that and on Linux this can be controlled via the cpufreq interface. I wrote a little daemon that simply checks every 5 seconds (adjustable) if the temperature is over a certain treshold (90 °C default, also adjustable) and if yes, it sets cpufreq to the powersave governor (which means lowest speed possible). When the temperature is below or at 90 °C again, it's set back to the (default) ondemand governor. It also works for more than one CPU (I have a dual core), though it's very likely that it has bugs as soon as one goes beyond 10 CPUs - but I have no way to test this. Feel free to report bugs.
This could be made more sophisticated (not going to the lowest frequency but step by step to lower frequencies), but it does its job quite well for now. It might be a good idea to support something like this directly in the kernel (I wonder why that isn't the case already - it's pretty obvious), but that would probably involve a skilled kernel-hacker.
I recently quite often had the problem that my system suddenly was shutting down. The reason was that when my processor got beyond 100 °C, my kernel decided that it's better to do so. I don't really know what caused this, but anyway, I needed a solution.
So i hacked together overheatd. A very effective way of cooling down a CPU is reducing its speed / frequency. Pretty much any modern CPU can do that and on Linux this can be controlled via the cpufreq interface. I wrote a little daemon that simply checks every 5 seconds (adjustable) if the temperature is over a certain treshold (90 °C default, also adjustable) and if yes, it sets cpufreq to the powersave governor (which means lowest speed possible). When the temperature is below or at 90 °C again, it's set back to the (default) ondemand governor. It also works for more than one CPU (I have a dual core), though it's very likely that it has bugs as soon as one goes beyond 10 CPUs - but I have no way to test this. Feel free to report bugs.
This could be made more sophisticated (not going to the lowest frequency but step by step to lower frequencies), but it does its job quite well for now. It might be a good idea to support something like this directly in the kernel (I wonder why that isn't the case already - it's pretty obvious), but that would probably involve a skilled kernel-hacker.
Thursday, September 9. 2010
Test your browser for Clickjacking protection
In 2008, a rather interesting new kind of security problem within web applications was found called Clickjacking. The idea is rather simple but genious: A webpage from the attacked web application is loaded into an iframe (a way to display a webpage within another webpage), but so small that the user cannot see it. Via javascript, this iframe is always placed below the mouse cursor and a button is focused in the iframe. When the user clicks anywhere on an attackers page, it clicks the button in his webapp causing some action the user didn't want to do.
What makes this vulnerability especially interesting is that it is a vulnerability within protocols and that it was pretty that there would be no easy fix without any changes to existing technology. A possible attempt to circumvent this would be a javascript frame killer code within every web application, but that's far away from being a nice solution (as it makes it neccessary to have javascript code around even if your webapp does not use any javascript at all).
Now, Microsoft suggested a new http header X-FRAME-OPTIONS that can be set to DENY or SAMEORIGIN. DENY means that the webpage sending that header may not be displayed in a frame or iframe at all. SAMEORIGIN means that it may only be referenced from webpages on the same domain name (sidenote: I tend to not like Microsoft and their behaviour on standards and security very much, but in this case there's no reason for that. Although it's not a standard – yet? - this proposal is completely sane and makes sense).
Just recently, Firefox added support, all major other browser already did that before (Opera, Chrome), so we finally have a solution to protect against clickjacking (konqueror does not support it yet and I found no plans for it, which may be a sign for the sad state of konqueror development regarding security features - they're also the only browser not supporting SNI). It's now up to web application developers to use that header. For most of them – if they're not using frames at all - it's probably quite easy, as they can just set the header to DENY all the time. If an app uses frames, it requires a bit more thoughts where to set DENY and where to use SAMEORIGIN.
It would also be nice to have some "official" IETF or W3C standard for it, but as all major browsers agree on that, it's okay to start using it now.
But the main reason I wrote this long introduction: I've set up a little test page where you can check if your browser supports the new header. If it doesn't, you should look for an update.
What makes this vulnerability especially interesting is that it is a vulnerability within protocols and that it was pretty that there would be no easy fix without any changes to existing technology. A possible attempt to circumvent this would be a javascript frame killer code within every web application, but that's far away from being a nice solution (as it makes it neccessary to have javascript code around even if your webapp does not use any javascript at all).
Now, Microsoft suggested a new http header X-FRAME-OPTIONS that can be set to DENY or SAMEORIGIN. DENY means that the webpage sending that header may not be displayed in a frame or iframe at all. SAMEORIGIN means that it may only be referenced from webpages on the same domain name (sidenote: I tend to not like Microsoft and their behaviour on standards and security very much, but in this case there's no reason for that. Although it's not a standard – yet? - this proposal is completely sane and makes sense).
Just recently, Firefox added support, all major other browser already did that before (Opera, Chrome), so we finally have a solution to protect against clickjacking (konqueror does not support it yet and I found no plans for it, which may be a sign for the sad state of konqueror development regarding security features - they're also the only browser not supporting SNI). It's now up to web application developers to use that header. For most of them – if they're not using frames at all - it's probably quite easy, as they can just set the header to DENY all the time. If an app uses frames, it requires a bit more thoughts where to set DENY and where to use SAMEORIGIN.
It would also be nice to have some "official" IETF or W3C standard for it, but as all major browsers agree on that, it's okay to start using it now.
But the main reason I wrote this long introduction: I've set up a little test page where you can check if your browser supports the new header. If it doesn't, you should look for an update.
Posted by Hanno Böck
in Code, English, Security
at
00:22
| Comment (1)
| Trackbacks (0)
Defined tags for this entry: browser, clickjacking, firefox, javascript, microsoft, security, vulnerability, websecurity
Friday, May 14. 2010
Secure RSA padding: RSA-PSS
I got selected for this years Google Summer of Code with a project for the implementation of RSA-PSS in the nss library. RSA-PSS will also be the topic of my diploma thesis, so I thought I'd write some lines about it.
RSA is, as you may probably know, the most widely used public key cryptography algorithm. It can be used for signing and encryption, RSA-PSS is about signing (something similar, RSA-OAEP, exists for encryption, but that's not my main topic).
The formula for the RSA-algorithm is S = M^k mod N (S is the signature, M the input, k the private key and N the product of two big prime numbers). One important thing is that M is not the Message itself, but some encoding of the message. A simple way of doing this encoding is using a hash-function, for example SHA256. This is basically how old standards (like PKCS #1 1.5) worked. While no attacks exist against this scheme, it's believed that this can be improved. One reason is that while the RSA-function accepts an input of size N (which is the same length as the keysize, for example 2048/4096 bit), hash-functions usually produce much smaller inputs (something like 160/256 bit).
An improved scheme for that is the Probabilistic Signature Scheme (PSS), (Bellare/Rogaway 1996/1998). PSS is "provable secure". It does not mean that the outcoming algorithm is "provable secure" (that's impossible with today's math), but that the outcome is as secure as the input algorithm RSA and the used hash function (so-called "random oracle model"). A standard for PSS-encryption is PKCS #1 2.1 (republished as RFC 3447) So PSS in general is a good idea as a security measure, but as there is no real pressure to implement it, it's still not used very much. Just an example, the new DNSSEC ressource records just published last year still use the old PKCS #1 1.5 standard.
For SSL/TLS, standards to use PSS exist (RFC 4055, RFC 5756), but implementation is widely lacking. Just recently, openssl got support for PSS verification. The only implementation of signature creation I'm aware of is the java-library bouncycastle (yes, this forced me to write some lines of java code).
The nss library is used by the Mozilla products (Firefox, Thunderbird), so an implementation there is crucial for a more widespread use of PSS.
RSA is, as you may probably know, the most widely used public key cryptography algorithm. It can be used for signing and encryption, RSA-PSS is about signing (something similar, RSA-OAEP, exists for encryption, but that's not my main topic).
The formula for the RSA-algorithm is S = M^k mod N (S is the signature, M the input, k the private key and N the product of two big prime numbers). One important thing is that M is not the Message itself, but some encoding of the message. A simple way of doing this encoding is using a hash-function, for example SHA256. This is basically how old standards (like PKCS #1 1.5) worked. While no attacks exist against this scheme, it's believed that this can be improved. One reason is that while the RSA-function accepts an input of size N (which is the same length as the keysize, for example 2048/4096 bit), hash-functions usually produce much smaller inputs (something like 160/256 bit).
An improved scheme for that is the Probabilistic Signature Scheme (PSS), (Bellare/Rogaway 1996/1998). PSS is "provable secure". It does not mean that the outcoming algorithm is "provable secure" (that's impossible with today's math), but that the outcome is as secure as the input algorithm RSA and the used hash function (so-called "random oracle model"). A standard for PSS-encryption is PKCS #1 2.1 (republished as RFC 3447) So PSS in general is a good idea as a security measure, but as there is no real pressure to implement it, it's still not used very much. Just an example, the new DNSSEC ressource records just published last year still use the old PKCS #1 1.5 standard.
For SSL/TLS, standards to use PSS exist (RFC 4055, RFC 5756), but implementation is widely lacking. Just recently, openssl got support for PSS verification. The only implementation of signature creation I'm aware of is the java-library bouncycastle (yes, this forced me to write some lines of java code).
The nss library is used by the Mozilla products (Firefox, Thunderbird), so an implementation there is crucial for a more widespread use of PSS.
Posted by Hanno Böck
in Code, Cryptography, English, Linux, Security
at
23:22
| Comments (0)
| Trackbacks (0)
Monday, April 5. 2010
Easterhegg in Munich
 I visited this year's easterhegg in Munich. The easterhegg is an event by the chaos computer club.
I visited this year's easterhegg in Munich. The easterhegg is an event by the chaos computer club.I held a talk expressing some thoughts I had in mind for quite a long time about free licenses. The conclusion is mainly that I think it very often may make more sense to use public domain "licensing" instead of free licenses with restrictions. The slides can be downloaded here (video recording here in high quality / 1024x576 and here in lower quality / 640x360). Talk was in german, but the slides are english. I plan to write down a longer text about the subject, but I don't know when I'll find time for that.
I also had a 5 minute lightning-talk about RSA-PSS and RSA-OAEP, slides are here (german). I will probably write my diploma thesis about PSS, so you may read more about that here in the future.
From the other talks, I want to mention one because I think it's a very interesting project about an important topic: The mySmartGrid project is working on an opensource based solution for local smart grids. It's a research project by Fraunhofer ITWM Kaiserslautern and it sounds very promising. Smart grids will almost definitely come within the next years and if people stick to the solutions provided by big energy companies, this will most likely be a big thread to privacy and will most probably prefer old centralized electricity generation.
Posted by Hanno Böck
in Code, Computer culture, Copyright, Ecology, English, Politics, Security
at
20:58
| Comments (4)
| Trackbacks (0)
Defined tags for this entry: ccc, copyright, easterhegg, licenses, mysmartgrid, publicdomain, rsa, rsaoaep, rsapss
Sunday, February 7. 2010
Free and open source developers meeting (FOSDEM)
 After reading a lot about interesting stuff happening at this years FOSDEM, I decided very short term to go there. The FOSDEM in Brussels is probably one of the biggest (if not the biggest at all) meetings of free software developers. Unlike similar events (like several Linuxtag-events in Germany), it's focus is mainly on developers, so the talks are more high level.
After reading a lot about interesting stuff happening at this years FOSDEM, I decided very short term to go there. The FOSDEM in Brussels is probably one of the biggest (if not the biggest at all) meetings of free software developers. Unlike similar events (like several Linuxtag-events in Germany), it's focus is mainly on developers, so the talks are more high level.My impressions from FOSDEM so far: There are much more people compared when I was here a few years ago, so it seems the number of free software developers is inceasing (which is great). The interest focus seems to be to extend free software to other areas. Embedded devices, the BIOS, open hardware (lot's of interest in 3D-printers).
Yesterday morning, there was a quite interesting talk by Richard Clayton about Phishing, Scam etc. with lots of statistics and info about the supposed business models behind it. Afterwards I had a nice chat with some developers from OpenInkpot. There was a big interest in the Coreboot-talk, so I (and many others) just didn't get in because it was full.
Later Gentoo-developer Petteri Räty gave a talk about "How to be a good upstream" and I'd suggest every free software developer to have a look on that (I'll put the link here later).
I've just attended a rather interesting talk about 3D-printers like RepRap and MakerBot.
Posted by Hanno Böck
in Code, Computer culture, Copyright, English, Gentoo, Life, Linux
at
10:34
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: fosdem fosdem2010 freesoftware linux reprap makerb
Friday, January 8. 2010
Videos aus ARD Mediathek herunterladen
Ich stand heute vor dem Problem, ein Video aus der ARD-Mediathek herunterladen zu wollen. Die gibt es meistens nur noch als Flash und ohne Download-Link.
Die Videos werden über RTMP übertragen, was ein Flash-eigenes Videostreaming-Protokoll ist. Im gulli-Forum fand ich eine Anleitung. Ich habe darauf basierend ein kleines Skript ardget geschrieben, mit dem man das bequem erledigen kann. Aufzurufen einfach über
ardget "[URL der Mediathek]"
Die Anführungszeichen sind notwendig, weil die URLs &-Zeichen enthalten, die sonst von der Shell fehlinterpretiert werden. Da die Videos teilweise mit Javascript-URLs verlinkt sind, filtere ich das auch entsprechend, man kann also den kompletten javascript: beginnenden Link übergeben. Benötigt wird entweder flvstreamer oder rtmpdump, sollte ansonsten in jeder gängigen Unix-Shell funktionieren.
Die Videos werden über RTMP übertragen, was ein Flash-eigenes Videostreaming-Protokoll ist. Im gulli-Forum fand ich eine Anleitung. Ich habe darauf basierend ein kleines Skript ardget geschrieben, mit dem man das bequem erledigen kann. Aufzurufen einfach über
ardget "[URL der Mediathek]"
Die Anführungszeichen sind notwendig, weil die URLs &-Zeichen enthalten, die sonst von der Shell fehlinterpretiert werden. Da die Videos teilweise mit Javascript-URLs verlinkt sind, filtere ich das auch entsprechend, man kann also den kompletten javascript: beginnenden Link übergeben. Benötigt wird entweder flvstreamer oder rtmpdump, sollte ansonsten in jeder gängigen Unix-Shell funktionieren.
Tuesday, January 13. 2009
Study research project about session cookies, SSL and session hijacking
In the last weeks, I made a study research project at the EISS at the University of Karlsruhe. The subject was »Session Cookies and SSL«, investigating the problems that arise when trying to secure a web application with HTTPS and using session cookies.
I already wrote about this in the past, presenting vulnerabilities in various web applications.
One of the notable results is probably that ebay has just no measurements against those issues at all, so it's pretty trivial to hijack a session (and use that to do bids and even change the address of the hijacked account).
Download »Session Cookies and SSL« (PDF, 317 KB)
I already wrote about this in the past, presenting vulnerabilities in various web applications.
One of the notable results is probably that ebay has just no measurements against those issues at all, so it's pretty trivial to hijack a session (and use that to do bids and even change the address of the hijacked account).
Download »Session Cookies and SSL« (PDF, 317 KB)
Saturday, December 13. 2008
A critique on the FSFE campaign on PDF readers
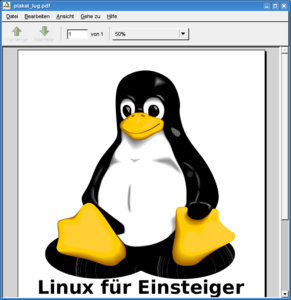 The Free Software Foundation Europe has recently started a campaign promoting free PDF readers. The idea is to replace the tons of »Get Adobe Reader to view the PDF«-Buttons with ones that don't promote a proprietary product for viewing PDFs. On the page, they list a couple of free PDF readers for various operating systems.
The Free Software Foundation Europe has recently started a campaign promoting free PDF readers. The idea is to replace the tons of »Get Adobe Reader to view the PDF«-Buttons with ones that don't promote a proprietary product for viewing PDFs. On the page, they list a couple of free PDF readers for various operating systems.While I fully support the intention of this campaign, I think there's a big strategic misconception. As a small sample, let's take this PDF (an old advertisement for a Linux installation party). It's created with Scribus, based on a transparent SVG tux image I got from Wikipedia. On the right, you can see the PDF rendered with Evince (one of the three Linux-based solutions listed there). The others (kpdf and okular), although based on the same poppler-libarary, show a different rendering, though it's not better.
 Loading the same PDF in the only listed Windows program SumatraPDF (which will, sad but true, probably the one most people will look for) gives an even more interesting result (see on the left). Though, after resizing the window, it changes it's opinion and renders the PDF, although still broken as you can see on the right (results may be false as I only tried it in WINE).
Loading the same PDF in the only listed Windows program SumatraPDF (which will, sad but true, probably the one most people will look for) gives an even more interesting result (see on the left). Though, after resizing the window, it changes it's opinion and renders the PDF, although still broken as you can see on the right (results may be false as I only tried it in WINE).Continuing with the problems, SumatraPDF is unable to fill in PDF forms. Luckily today Linux-based PDF readers are able to do that, though one of the listed programs (kpdf) is not.
 In fact, those are no reasons not to start a campaign for free PDF readers. But it should start with a completely different focus, like »we have some coders wanting to improve free PDF readers, send us your wrong rendered PDFs« or something like that. And then start improving the free PDF readers. And then promote them. Doing it the other way round with a »there is no problem, just take a free PDF reader« message and then giving them ones with grave problems is just lying to people. There's a good reason why for example the Scribus project promotes the Adobe Reader.
In fact, those are no reasons not to start a campaign for free PDF readers. But it should start with a completely different focus, like »we have some coders wanting to improve free PDF readers, send us your wrong rendered PDFs« or something like that. And then start improving the free PDF readers. And then promote them. Doing it the other way round with a »there is no problem, just take a free PDF reader« message and then giving them ones with grave problems is just lying to people. There's a good reason why for example the Scribus project promotes the Adobe Reader.Oh, and before you ask, yes, I have reported the bug about the misrendered transparency a long time ago.
Posted by Hanno Böck
in Code, Copyright, Linux
at
13:35
| Comments (0)
| Trackbacks (0)
Defined tags for this entry: adobe, evince, freesoftware, fsfe, kpdf, okular, pdf, poppler, sumatrapdf
Sunday, September 7. 2008
Fuzzing is easy
I recently played around with the possibilities of fuzzing. It's a simple way to find bugs in applications.
What you do: You have some application that parses some kind of file format. You create lots (thousands) of files which have small errors. The simplest approach is to just change random bits. If the app crashes, you've found a bug, it's quite likely that it's a security relevant one. This is especially crucial for apps like mail scanners (antivirus), but pretty much works for every app that parses foreign input. It works especially well on uncommon file formats, because their code is often not well maintained.
My fuzzing tool of choice is zzuf.
I am impressed and a bit shocked how easy it is to find crashers and potential overflows in common, security relevant applications. My last discovery was a crasher in the chm parser of clamav.
What you do: You have some application that parses some kind of file format. You create lots (thousands) of files which have small errors. The simplest approach is to just change random bits. If the app crashes, you've found a bug, it's quite likely that it's a security relevant one. This is especially crucial for apps like mail scanners (antivirus), but pretty much works for every app that parses foreign input. It works especially well on uncommon file formats, because their code is often not well maintained.
My fuzzing tool of choice is zzuf.
I am impressed and a bit shocked how easy it is to find crashers and potential overflows in common, security relevant applications. My last discovery was a crasher in the chm parser of clamav.
Saturday, July 5. 2008
GPN7 and surveillance cameras in OpenStreetMap
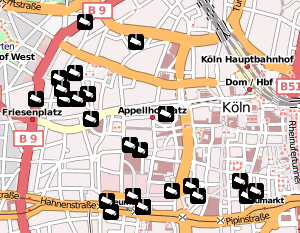 It's the second day on the GPN7 (a local hacker event from the Chaos Computer Club Karlsruhe / Entropia).
It's the second day on the GPN7 (a local hacker event from the Chaos Computer Club Karlsruhe / Entropia).Yesterday evening I hacked together a map based on openstreetmap showing surveillance cameras:
http://osm-cctv.hboeck.de/
As a basis, we could use some data provided by the chaos computer club cologne. I'm working on an importer to get that into the openstreetmap database. Will probably happen within the next days.
All cameras tagged with man_made=surveillance in germany.osm are already imported into the overlay. I'll keep a wiki-page up-to-date at:
http://wiki.openstreetmap.org/index.php/User:Hanno/CCTV
Posted by Hanno Böck
in Code, Computer culture, English, Politics
at
15:01
| Comments (0)
| Trackback (1)
Defined tags for this entry: c4, ccc, cctv, datenschutz, entropia, gpn, gpn7, openstreetmap, privacy, surveillance, überwachung, überwachungskameras
Tuesday, June 17. 2008
Linux on a Wii
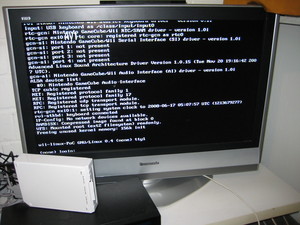 Today I played around a bit with the stuff done by the Wii homebrew/hacking community, which is far more advanced than I had expected.
Today I played around a bit with the stuff done by the Wii homebrew/hacking community, which is far more advanced than I had expected.I had the game Twilight Princess borrowed by a friend. For those who don't know, using this game you can run homebrew software on the Wii without the need of a modchip.
 The way this works is that first you install a modified savegame for Twilight Princess, afterwards you can install the Homebrew Channel. The Homebrew Channel will stay in the main Wii Menu and you'll be able to run various stuff from there. While looking around the various webpages covering the topic, I found that wiibrew.org is a good place to find documentation and links to the appropriate projects. So look there for the details.
The way this works is that first you install a modified savegame for Twilight Princess, afterwards you can install the Homebrew Channel. The Homebrew Channel will stay in the main Wii Menu and you'll be able to run various stuff from there. While looking around the various webpages covering the topic, I found that wiibrew.org is a good place to find documentation and links to the appropriate projects. So look there for the details.The gc-linux project (originally porting linux to the gamecube) has a simple Linux image available.
A warning: Nintendo released a new firmware that stops this method to work, so if you wanna have fun, don't update your Wii. And the obvious warning: Everything you do is at your own risk.
Update: Seems the Firmware update is no longer a problem.
Posted by Hanno Böck
in Code, Computer culture, English, Gentoo, Linux
at
23:52
| Comments (3)
| Trackback (1)
« previous page
(Page 2 of 5, totaling 66 entries)
» next page