Tuesday, April 29. 2008
Hash-collissions in real world scenarios
I just read an article about the recent wordpress vulnerability (if you're running wordpress, please update to 2.5.1 NOW), one point raised my attention: The attack uses MD5-collisions.
I wrote some articles about hash collisions a while back. Short introduction: A cryptographic hash-function is a function where you can put in any data and you'll get a unique, fixed-size value. »unique« in this case scenario means that it's very hard to calculate two different strings matching to the same hash value. If you can do that, the function should be considered broken.
The MD5 function got broken some years back (2004) and it's more or less a question of time when the same will happen to SHA1. There have been scientific results claiming that an attacker with enough money could easily create a supercomputer able to create collisions on SHA1. The evil thing is: Due to the design of both functions, if you have one collision, you can create many more easily.
Although those facts are well known, SHA1 is still widely used (just have a look at your SSL connections or at the way the PGP web of trust works) and MD5 isn't dead either. The fact that a well-known piece of software got issues depending on hash collisions should raise attention. Pretty much all security considerations on cryptographic protocols rely on the collision resistance of hash functions.
The NIST plans to define new hash functions until 2012, until then it's probably a safe choice to stick with SHA256 or SHA512.
I wrote some articles about hash collisions a while back. Short introduction: A cryptographic hash-function is a function where you can put in any data and you'll get a unique, fixed-size value. »unique« in this case scenario means that it's very hard to calculate two different strings matching to the same hash value. If you can do that, the function should be considered broken.
The MD5 function got broken some years back (2004) and it's more or less a question of time when the same will happen to SHA1. There have been scientific results claiming that an attacker with enough money could easily create a supercomputer able to create collisions on SHA1. The evil thing is: Due to the design of both functions, if you have one collision, you can create many more easily.
Although those facts are well known, SHA1 is still widely used (just have a look at your SSL connections or at the way the PGP web of trust works) and MD5 isn't dead either. The fact that a well-known piece of software got issues depending on hash collisions should raise attention. Pretty much all security considerations on cryptographic protocols rely on the collision resistance of hash functions.
The NIST plans to define new hash functions until 2012, until then it's probably a safe choice to stick with SHA256 or SHA512.
Posted by Hanno Böck
in Code, Cryptography, English, Security
at
21:44
| Comments (3)
| Trackbacks (0)
Wednesday, April 23. 2008
Free software for your canon camera (CHDK)
 I own this Canon IXUS 50 camera for more than two years now. It's a fine device, but it has some small lacking features where I often asked myself if this could be enhanced with a new firmware.
I own this Canon IXUS 50 camera for more than two years now. It's a fine device, but it has some small lacking features where I often asked myself if this could be enhanced with a new firmware.Until recently, when I read about the CHDK project: It's a kind of firmware enhancements for Canon cameras. It doesn't fully replace the real firmware, but adds additional stuff (I must say I don't fully understand what they do). And now they have an experimental port for the SD400, which is built into my cam.
The first big killerfeature one will notice is that the cam now has a battery monitor, which is the most obvious lacking feature of the original firmware.
One more thing I always would've liked for my cam is a better video compression. The video quality is quite good, but the cam just can do mjpeg, which leads to big files and limits your maximum video size to about 20 minutes. It seems CHDK has some better compression video mode, but I'll have to dig deeper into it. Beside, I can now record raw images. So there's lot's of cool stuff to play with.
Monday, April 21. 2008
gajim with otr encryption
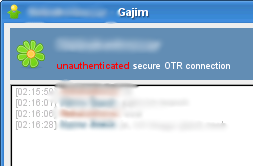 In the instant messaging world, encryption is a bit of a problem. There is no single standard that all clients share, mostly two methods of encryption are out there: pgp over jabber (as defined in the xmpp standard) and otr.
In the instant messaging world, encryption is a bit of a problem. There is no single standard that all clients share, mostly two methods of encryption are out there: pgp over jabber (as defined in the xmpp standard) and otr.Most clients only support either otr (pidgin, adium) or pgp (gajim, psi), for a long time I was looking for a solution where both methods work. psi has otr-patches, but they didn't work when I tried them. kopete also has an otr-plugin, but I've not tested that yet.
Today I found that there is an otr-branch of gajim, which is my everyday client, so this would be great. As you can see on the picture, it seems to work on a connection with an ICQ user using pidgin.
I've created some ebuilds in my overlay (the code is stored in bazaar, I've copied the bzr eclass from the desktop effects overlay):
svn co https://svn.hboeck.de/overlay
ping with IDN
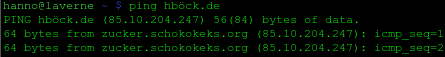 Today I asked myself if I can ping an IDN host.
Today I asked myself if I can ping an IDN host.My default ping (iputils on linux) couldn't do it, but I found some patches out there, e.g. from Fedora. Thanks to SpanKY, we now also have IDN-enabled ping in Gentoo (he used a modified patch).
Posted by Hanno Böck
in Computer culture, English, Gentoo, Linux
at
01:26
| Comments (2)
| Trackbacks (0)
Thursday, April 10. 2008
Wordpress mass hacks for pagerank
Today heise security brought a news that a growing number of old wordpress installations get's misused by spammers to improve their pagerank. I've more or less waited for something like that, because it's quite obvious: If you have an automated mechanism to use security holes in a popular web application, you can search for them with a search engine (google, the mighty hacktool) and usually it's quite trivial to detect both application and version.
This isn't a wordpress-thing only, this can happen to pretty much every widespread web application. Wordpress had a lot of security issues recently and is very widespread, so it's an obvious choice. But other incidents like this will follow and future ones probably will affect more different web applications.
The conclusion is quite simple: If you're installing a web application yourself, you are responsible for it! You need to look for security updates and you need to install them, else you might be responsible for spammers actions. And there's no »nobody is interested in my little blog«-excuse, as these are not attacks against an individual page, but mass attacks.
For administrators, I wrote a little tool a while back, where I had such incidents in mind: freewvs, it checks locally on the filesystem for web applications and knows about vulnerabilities, so it'll tell you which web applications need updates. It already detects a whole bunch of apps, while more is always better and if you'd like to help, I'd gladly accept patches for more applications (the format is quite simple).
With it, server administrators can check the webroots of thier users and nag them if they have outdated cruft laying around.
This isn't a wordpress-thing only, this can happen to pretty much every widespread web application. Wordpress had a lot of security issues recently and is very widespread, so it's an obvious choice. But other incidents like this will follow and future ones probably will affect more different web applications.
The conclusion is quite simple: If you're installing a web application yourself, you are responsible for it! You need to look for security updates and you need to install them, else you might be responsible for spammers actions. And there's no »nobody is interested in my little blog«-excuse, as these are not attacks against an individual page, but mass attacks.
For administrators, I wrote a little tool a while back, where I had such incidents in mind: freewvs, it checks locally on the filesystem for web applications and knows about vulnerabilities, so it'll tell you which web applications need updates. It already detects a whole bunch of apps, while more is always better and if you'd like to help, I'd gladly accept patches for more applications (the format is quite simple).
With it, server administrators can check the webroots of thier users and nag them if they have outdated cruft laying around.
Posted by Hanno Böck
in Computer culture, English, Linux, Security
at
02:44
| Comment (1)
| Trackbacks (0)
(Page 1 of 1, totaling 5 entries)