Friday, June 6. 2014
Enabling encryption by default and using HTTPS only
Comments
Display comments as
(Linear | Threaded)
Your blog is public.
Any information on it can be accessed by anyone. Public copies are available from Google Cache and elsewhere. Nobody needs to type in their email address in a comment if they feel that's secret information. And they would not change opinion because of SSL. I doubt they trust your MySQL on that shared Hetzner box more than your Class 2 Cert from StartCom. So there is no content to protect (secrecy aspect of security). Integrity is not an issue as there is no realistic attack scenario that would compromise communication to your site to inject e.g. a fake blog entry. But Availability is an issue as you want to reach as many users as possible. That's probably why you blog in the first place. Your audience includes people on Android and Russian native speakers that use Yandex to find your content. Or people that use simple RSS feed readers that choke on your SSL setup. Or any SSL setup. So forcing SSL for non-authenticate users (so not your Serendipity /admin) is counter-productive. It's a "but, but ... I need to do something" reaction of the helpless geek in the Post-Snowdon era.
The only - slight advantage - I can see is that most spam bots won't bother with your TLS setup. So you get less spam. But I doubt that's worth it.
BTW: You're not protecting users from injected scripts through making your content any "securely" available.
1) That would only be worth it if there wasn't any other sites your users access in plain HTTP and
2) SSL certs would be worth anything still.
You also include plain http content. E.g. http://api.flattr.com/js/0.6/load.js so that's easy to man-in-the middle and get a script loaded into your "secure" DOM.
Any information on it can be accessed by anyone. Public copies are available from Google Cache and elsewhere. Nobody needs to type in their email address in a comment if they feel that's secret information. And they would not change opinion because of SSL. I doubt they trust your MySQL on that shared Hetzner box more than your Class 2 Cert from StartCom. So there is no content to protect (secrecy aspect of security). Integrity is not an issue as there is no realistic attack scenario that would compromise communication to your site to inject e.g. a fake blog entry. But Availability is an issue as you want to reach as many users as possible. That's probably why you blog in the first place. Your audience includes people on Android and Russian native speakers that use Yandex to find your content. Or people that use simple RSS feed readers that choke on your SSL setup. Or any SSL setup. So forcing SSL for non-authenticate users (so not your Serendipity /admin) is counter-productive. It's a "but, but ... I need to do something" reaction of the helpless geek in the Post-Snowdon era.
The only - slight advantage - I can see is that most spam bots won't bother with your TLS setup. So you get less spam. But I doubt that's worth it.
BTW: You're not protecting users from injected scripts through making your content any "securely" available.
1) That would only be worth it if there wasn't any other sites your users access in plain HTTP and
2) SSL certs would be worth anything still.
You also include plain http content. E.g. http://api.flattr.com/js/0.6/load.js so that's easy to man-in-the middle and get a script loaded into your "secure" DOM.
Actually there are some real gains from using HTTPS even on public read-only websites. One is protecting all kinds of metadata. An attacker will still see that someone is reading my blog, but he won't see what subpages someone is accessing. Also HTTPS protects from modification of the webpage content by an active adversary (which could be everything from changing texts to embedding malware).
But I admit these are most likely minor issues. The reason I'm doing this is that I think we need early adopters for encryption by default. I am deeply convinced we need to get more and better crypto out of the door. Unlike large webpage providers I can afford to loose a few readers and I still can help out identifying potential problems. I started 10 years ago enabling TLS-only-access to our mail servers, recently most large German mail providers followed.
Btw., I'm not on a shared hosting Hetzner service, I'm running my own web hosting (which runs on Hetzner servers, but these run an operating system I fully control except for physical access).
Regarding flattr you have a point, however as most browser block mixed content the flattr button probably just won't work for most visitors right now. I'll try to fix that (probably the s9y plugin should be changed to use protocol relative references here).
But I admit these are most likely minor issues. The reason I'm doing this is that I think we need early adopters for encryption by default. I am deeply convinced we need to get more and better crypto out of the door. Unlike large webpage providers I can afford to loose a few readers and I still can help out identifying potential problems. I started 10 years ago enabling TLS-only-access to our mail servers, recently most large German mail providers followed.
Btw., I'm not on a shared hosting Hetzner service, I'm running my own web hosting (which runs on Hetzner servers, but these run an operating system I fully control except for physical access).
Regarding flattr you have a point, however as most browser block mixed content the flattr button probably just won't work for most visitors right now. I'll try to fix that (probably the s9y plugin should be changed to use protocol relative references here).
Interesting!
However to me it looks like the YandexBot does speak SNI and TLS 1.0:
https://www.ssllabs.com/ssltest/viewClient.html?name=YandexBot&version=May%202014
However to me it looks like the YandexBot does speak SNI and TLS 1.0:
https://www.ssllabs.com/ssltest/viewClient.html?name=YandexBot&version=May%202014
Then it seems things have improved. Good to know.
When I wrote this blog entry the Qualys test showed me no connection to the Yandex bot.
When I wrote this blog entry the Qualys test showed me no connection to the Yandex bot.
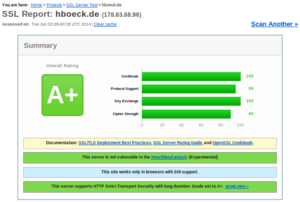 I recently switched my personal web page and my blog to deliver content exclusively encrypted via HTTPS. I want to take this opportunity to give some facts about enabling TLS encryption by default and problems you may face.
I recently switched my personal web page and my blog to deliver content exclusively encrypted via HTTPS. I want to take this opportunity to give some facts about enabling TLS encryption by default and problems you may face.
Seit einem Jahr läuft dieses Blog (und sämtliche anderen Seiten auf crashmail.de) nun mittlerweile als https-only. Ich nutze dafür StartCom Class1 Zertifikate, die eine Gültigkeit von einem Jahr haben und dann erneuert werden müssen. Über das Für und Wide
Tracked: Jun 08, 08:02