Monday, February 23. 2015
Software Privdog worse than Superfish
Comments
Display comments as
(Linear | Threaded)
"(with some trickery you can do something similar on Superfish/Komodia, too)"
No trickery needed whatsoever. All you need is a WiFi Pineapple with the SSLSplit infusion and this is what bothers me the most. It's quite possible real bad guys have been MitMing Superfish and other products from Komodia or that use Comodia without even trying. For what it's worth, I had the original discovery on what Komodia was doing with the SAN but held off on a full write-up, rather I posted a bit of a heads-up to HN while I worked with the vendor:
https://news.ycombinator.com/item?id=9078536
No trickery needed whatsoever. All you need is a WiFi Pineapple with the SSLSplit infusion and this is what bothers me the most. It's quite possible real bad guys have been MitMing Superfish and other products from Komodia or that use Comodia without even trying. For what it's worth, I had the original discovery on what Komodia was doing with the SAN but held off on a full write-up, rather I posted a bit of a heads-up to HN while I worked with the vendor:
https://news.ycombinator.com/item?id=9078536
Heh, recently we were looking for ssl certificates and I specifically recommended against comodo because I heard bad things about it. Looks like I was right :D
Many people are using Comodo Firewall, which provides better security than Windows Firewall.
On the late 2014 update(if I remember correctly), Comodo start installing PrivDog to
Comodo Firewall's user computer without notice.
If you're ignoring(or blocking) comodo update(>= v7), you are safe from stupid
dog unless you install it separately.
v6 and older are safe to use.
So, Privdog affects many PCs... more than Lenovo scandal I guess.
Let's see other people yell to comodo developers on the "Comodo Forum"...
On the late 2014 update(if I remember correctly), Comodo start installing PrivDog to
Comodo Firewall's user computer without notice.
If you're ignoring(or blocking) comodo update(>= v7), you are safe from stupid
dog unless you install it separately.
v6 and older are safe to use.
So, Privdog affects many PCs... more than Lenovo scandal I guess.
Let's see other people yell to comodo developers on the "Comodo Forum"...
Also antiviur Avast is doing the same [http://security.stackexchange.com/questions/72535/avast-https-scanning]
What Avast is doing is not the same. They generate a cert on every installation and they verify server certs.
I still think this is a bad approach, but it is not as severely broken as Superfish/Privdog. It does for example circumvent HPKP.
I still think this is a bad approach, but it is not as severely broken as Superfish/Privdog. It does for example circumvent HPKP.
Comodo only 'ships' this service / plugin as part of the Chromium browser, and it's transparent to the user as a plugin - it can be disabled.
It doesn't turn your existing browser into an SSL accepting / root signing certificate troll!
If you use Comodo services, it does not mean you're suddenly susceptible to this attack. I'd air on the side of safety and not use the Comodo Chromium browser though - at least until Comodo release their own response to the threat.
It doesn't turn your existing browser into an SSL accepting / root signing certificate troll!
If you use Comodo services, it does not mean you're suddenly susceptible to this attack. I'd air on the side of safety and not use the Comodo Chromium browser though - at least until Comodo release their own response to the threat.
I used to use and trust Comodo products. I no longer trust your products because of what I have read about PrivDog [all iterations]
bof
I stopped using comodo firewall some years ago.
found it a wonderfull firewall, strong versus attack, efficent user interface, really nice rules regulation and so on.
Then I had to uninstall the old version to install the new.
The uninstall broke my hard disk.
And I don't mean I had to format.
I had to change the hard disk since it burned some clusters.
Now, this was some seven uears ago, I think.
I'm sure they did clean up their uninstaller.
Still I will never use that firewall ever again.
I stopped using comodo firewall some years ago.
found it a wonderfull firewall, strong versus attack, efficent user interface, really nice rules regulation and so on.
Then I had to uninstall the old version to install the new.
The uninstall broke my hard disk.
And I don't mean I had to format.
I had to change the hard disk since it burned some clusters.
Now, this was some seven uears ago, I think.
I'm sure they did clean up their uninstaller.
Still I will never use that firewall ever again.
I no longer trust any of Comodo's products. I've used their firewall software on few of my PCs based on recommendation by certain websites. I never liked the software to begin with but thought it was giving me better protection than the built-in windows firewall. I always had a nagging feeling as to how they are making money. Anyway I got rid of their software since some of it's behavior didn't sit well with me. I convinced a couple of my relatives and friends to do the same.
I remember the time when the internet was pure and clean, in it's virgen like days.
Now it's more like a tramp, that screws you over, takes your money and leaves you with a bad feeling.
Oh, and you keep comming back, of cource.
.-(
Now it's more like a tramp, that screws you over, takes your money and leaves you with a bad feeling.
Oh, and you keep comming back, of cource.
.-(
It's not only Comodo which is practicing that method.
Avast, BitDefender, Kaspersky, ESET, Dr. Web, Symantec -- some vendors that you will notice if you analyze it. Do not point a finger at one but at many.
Avast, BitDefender, Kaspersky, ESET, Dr. Web, Symantec -- some vendors that you will notice if you analyze it. Do not point a finger at one but at many.
Scheint so als würde deine Testseite superfish.tlsfun.de nicht mehr richtig funktionieren? Übrigens nebenbei: der HKPK bug in Arch Linux wurde vor wenigen Tagen behoben. Diesen Kommentar gerne löschen bzw. nicht freischalten.
 tl;dr There is a software called Privdog. It totally breaks HTTPS security in a similar way as Superfish.
tl;dr There is a software called Privdog. It totally breaks HTTPS security in a similar way as Superfish.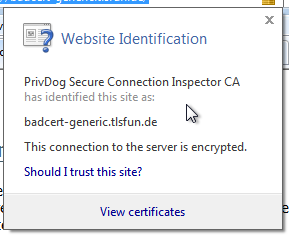 US-CERT
US-CERT
Tracked: Feb 23, 05:43
Tracked: Feb 23, 08:28
Tracked: Feb 23, 15:07
Tracked: Feb 23, 17:53
Tracked: Feb 23, 20:16
Tracked: Feb 24, 06:34
Tracked: Feb 24, 07:32
Tracked: Feb 24, 09:04
Tracked: Feb 24, 12:32
Tracked: Feb 24, 14:50
Tracked: Feb 24, 15:50
Tracked: Feb 25, 03:15
tl;dr PrivDog will send webpage URLs you surf to a server owned by Adtrust Media. This happened unencrypted in cleartext HTTP. This is true for both the version that is shipped with some Comodo products and the standalone version from the PrivDog webpage.
Tracked: Feb 25, 23:00
Tracked: Feb 26, 10:01
「Lenovo は何をやらかしたのか」から改題し,修正・追記しています。(2月26日)
Tracked: Feb 26, 12:36
Tracked: Feb 28, 21:23
Tracked: Mar 02, 13:04
Tracked: Mar 02, 18:21
Tracked: Mar 03, 18:16
Tracked: Mar 31, 19:17
Tracked: Apr 06, 15:26
Lately a lot of attention has been payed to software like Superfish and Privdog that intercepts TLS connections to be able to manipulate HTTPS traffic. These programs had severe (technically different) vulnerabilities that allowed attacks on HTTPS connect
Tracked: Apr 26, 19:50
In February the discovery of a software called Superfish caused widespread attention. Superfish caused a severe security vulnerability by intercepting HTTPS connections with a Man-in-the-Middle-certificate. The certificate and the corresponding private ke
Tracked: Aug 13, 00:45
tl;dr Dell laptops come preinstalled with a root certificate and a corresponding private key. That completely compromises the security of encrypted HTTPS connections. I've provided an online check, affected users should delete the certificate. It seems
Tracked: Nov 23, 17:39